The retail industry has seen tremendous growth in the past few years with every business establishing its online presence. However, the access to a vast online customer pool also affects the cybercrime landscape of the retail industry. Phishing, now augmented with artificial intelligence technology, is one of the primary modes used to propagate a variety of cyberattacks such as ransomware, malware, social engineering, and more. With the holiday season upon us, swarms of shoppers are combing the Internet for online deals. With all these online transactions taking place, there’s much greater opportunity for holiday retail scams.
From a batch of over 4000 domains observed from late October through early December 2024 (including a few registered earlier this year), researchers at BforeAI identified over 3000 domains that were suspicious in nature and 2709 that were malicious, meaning they engaged in phishing attacks using holiday retail themes. These domains were largely based on keyword matches and covered significant events such as Halloween, Thanksgiving, Black Friday, Cyber Monday, Christmas, and New Year celebrations.
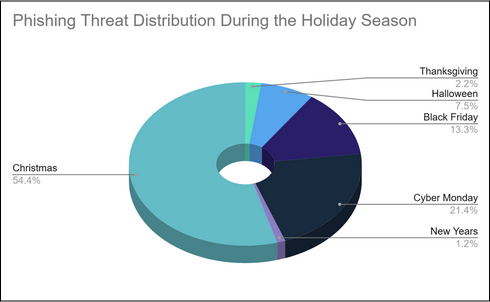
The threat distribution is as follows:
Holiday | Threat Count |
Halloween | 189 |
Thanksgiving | 56 |
Black Friday | 338 |
Cyber Monday | 543 |
Christmas | 1379 |
New Year | 30 |
Holiday-based phishing in retail industry: Generic trends
The convenience of ecommerce shopping directly impacts the rise of cyberthreats on this industry, given that retail websites interact with a large number of customers.
Out of 2709 confirmed suspicious domains, 1821 domains were registered in 2024, with some still active as of December 2024. A phishing domain deviating from the typical typosquatting pattern, by directly combining a holiday event or opportunity with a retailer’s name. For example, we saw Walmart combined with “gift cards” over mistaken spellings: binance-identification.giftstore[.]ng, airflow.get-free-walmart[.]gifts, etc.
Most of the domains overlapped different events bound in the same domain name, for example, blackfridaycybermondaydeals[.]com, thanksgivingblackfridayads[.]com.
Thanksgiving-based holiday scams
With keywords directly matching “Thanksgiving”, we saw 33 confirmed suspicious domains promoting domain abuse, betting, and email phishing through parked domains. Threat actors used the term “Thanksgiving” with random alphanumeric characters, and some instances included giant retailers such as Walmart.
A set of giveaway domains were observed that offered high-value items such as Tesla and Apple gift cards, a common phishing tactic to lure victims. These scams have the potential to cause hefty financial losses for unsuspecting customers.
We observed some generic domain names using “Thanksgiving” in their webpage titles and URLs, but hosting irrelevant content on the website. This hints towards them being time-bound malicious infrastructures that conclude after the holiday season. However, given the generic nature of domain names, they may also be activated in the future for phishing across multiple industries.
Black Friday and Cyber Monday-based holiday scams
Leading up to and on Black Friday, we observed a set of domains registered earlier this year that became actively operational shortly before the event date. The tactic of making the site operational shortly before helps malicious sites to evade detection, while the older registration date aids them to rank well on search engines. Domains were registered in the “blackfriday-x” pattern where “x” is the placeholder for most of the items that could be found in the retail store.
In early November, a batch of Black Friday domains were registered with the “.bond” top level domain (TLD) and random characters, indicating efforts to maintain the continuity of a campaign in the event some of them are detected. Another set of domains used supporting keywords such as “deals”, “coupons”, “guides”, “TV”, “tablets”, “heaters”, “vacuum cleaners”, and other items found in electronics stores to attract shopping enthusiasts. Notably, the well-known and popular fashion brand Lululemon was used with this event as well.
The same deal was seen for the Cyber Monday sale, where TLDs such as “.today”, “.click”, and “.sale” were observed attempting to leverage a sense of urgency among users.
Christmas-based holiday scams
The Christmas holiday attracts a high concentration of cyberattacks, with the highest number of phished domains for the overall season. Cybercriminals exploit the festive spirit by focusing their retail scams on sale and purchase offers, including Christmas trees, decor services, and giveaways for free items.
Christmas and New Year scam content is also about corporate gifting, and a handful of domains mentioned “Gifts for Companies”, hosting fraudulent offers for bulk purchases of company gifts, posing a serious threat to businesses.
Christmas-based scams: Case study
The Alzensep Campaign
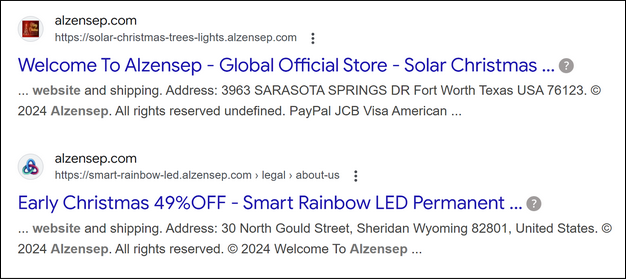
During our research, we came across 291 subdomains registered under the root domain, “alzensep[.]com”, which appears to be a suspicious online retail store targeting global customers. This store attempts to offer a wide range of products under the pretenses of early Christmas sales and claims to be from the United States. However, upon in-depth investigation, the website was created a mere 9 months ago, in February 2024. The registrant and administrative details for this website is from 204 Thanh Xuan, Hanoi, Vietnam.
This website lacks a verifiable home page and social media presence, unlike traditional ecommerce retail stores. At the time of this report, there are 291 different products being promoted on this website. It is also interesting to note that the address of this store keeps changing, depending on the subdomain that the users are looking at. These are some indicators that highlight the suspicious behavior of the store in question.
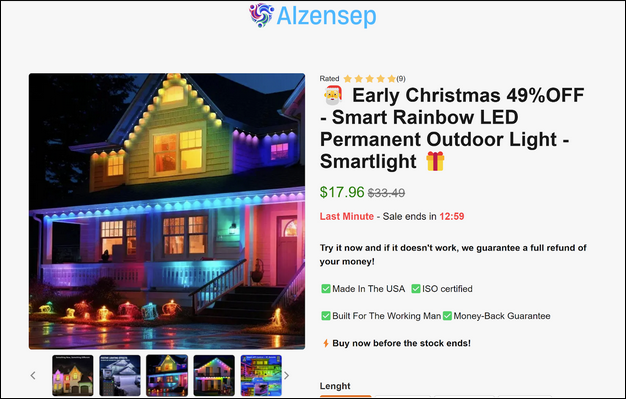
This store has no credible reviews or significant social media presence. The logo of this store keeps dynamically changing depending on the subdomain or the product being advertised.
The domain (screenshot below) targets the popular Indian payments provider, PhonePe. Victims were tricked into entering their phone number to earn recharge offers, but was a ploy aimed at financial fraud and harvesting number data.

Domain: newyeardealsforyou.online
New Year-based holiday scams
New Year based phishing domains leveraged DNS abuse by distributing fake apps, and suspicious chrome extensions. Again, Walmart and its subsidiary Flipkart, which has large operations in India, were on cybercriminals’ radar to promote free gift card scams in holiday and gift giving season.
Deviating from the typical retail brands, the researchers also investigated Apple gift card giveaways. Some of these domains were programmed to load its malicious content only when the victim’s device works on a particular operating system, for example, Apple’s iOS.
One such domain was found to promote malicious app downloads, primarily targeting users in Turkey. This highlights the spread of New Year scams on a global level. Unlike traditional phishing attacks, these domains make use of a more elongated strategy. Instead of directly targeting personal or financial information, they focus on delivering malicious apps through phishing pages.
The domain below, targeting Turkish users, offered an app for downloading, which is suspected of delivering malware or trojan files. Interestingly, this app is based on Christmas events, but the domain is focused on New Year celebrations, creating an overlap of events. Such apps stealthily collect sensitive data from victim’s devices who download it.
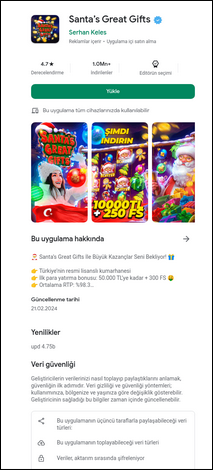
Domain: newyearturkish.cfd
Why are there so many scams around the holiday season in the retail industry?
Holiday season comes with extended breaks, which further affects organizational security more than usual. Increased work load, lack of attention to the security posture along with decreased round the clock availability, are some of the factors to explain why the holiday season is a peak time for scams. This can result in missed opportunities in addressing the best cybersecurity practices from scalability and continuous threat monitoring.
The research clearly indicates that larger retailers with a high level of brand awareness and popularity are prime targets for cybercriminals, such as Walmart, Flipkart, Apple, and Tesla. Their strong reputation and large customer base lead to increased visibility, making phishing attempts successful as compared to smaller and mid-sized businesses.
Customers affecting the security posture of the retail industry
With increased online shopping, there’s an equivalent rise in sophisticated phishing attacks across different vectors such as spoofed web pages, QR codes, transaction pages, and emails.
During these festive times, consumers tend to let their guard down, not taking the time and effort required to validate websites or links to ensure they originate from legitimate businesses.
For shoppers, the emotional intensity, time-sensitive nature of holiday gift-giving, and the urgency of grabbing the deal while it lasts leads to hasty decision making, all of which is leveraged by cybercriminals. On average, individuals who are less active online shoppers may also be less familiar with the threats lurking in the shadows. When these users become more active during the holiday season they might be unable to differentiate between valid and spoofed domains, leading to an increased risk of falling victim to scams.
How to mitigate retail phishing scams during the holiday season?
Organizational readiness in handling scams around the holiday season includes continuous monitoring and preemptive threat mitigation to stop an adversarial infrastructure before it can be established or launched. This implies predicting re-registered and newly-registered suspicious domains and determining their maliciousness based on different indicators.
Customers who love shopping the holiday sales should be aware of any unsolicited communication popping on their devices, whether they be through emails, SMS, or search engines. Unless the authenticity of a deal, or indirectly the brand being advertised is verified, it should be approached with caution. Common steps to ensure user safety would be:
- Checking for the “HTTPS” status and registration dates of the domains with resources like https://www.google.com/url?q=https://www.whois.com/whois, since well-known brands won’t interact with newly created domain names.
- Taking time to notice common signs of typosquatting, such as replacing correct characters with similarly-shaped incorrect ones to make the domain name mimic the original.
- Verifying the payment processor on the transactions page and ensuring the recipient details to whom the payment is being made.
- Steering clear of any app that asks for sensitive information as a requirement to obtain free coupons or giveaways during holiday sales.