How scammers inject content into benign websites via Google Ads
Scammers are always on the lookout for new tricks to deceive people and spread their scams.
In recent years, we’ve seen a surge in malicious online ads that lure users into clicking by promising huge discounts, fake investment opportunities, or even displaying scary warnings about supposed viruses or problems on their devices. These ads typically lead users to scam websites controlled by fraudsters, where the scam unfolds. In certain scams, such as fake investment schemes and tech support scams / fraud, scammers quickly steer victims to continue the conversation over the phone.
Recently, researchers at BforeAI discovered a new twist on this tactic, one specifically designed to promote tech support scams. Scammers exploit Google search ads to target people looking for tech support for well-known brands like Microsoft and Facebook. Instead of redirecting users to fake websites, these ads redirect users to the official pages of the targeted brands.
Here’s how it works:
When someone searches for tech support and clicks on one of these scam ads, they are taken to the real website of the brand, not a fake one. However, scammers exploit vulnerabilities in the website’s internal site search function to inject their fake customer support phone numbers into the search results.
Many websites offer an internal site search feature to help visitors find content within the site. However, scammers take advantage of poor sanitization in these internal search engines, allowing them to insert their own content, like fraudulent tech support numbers, directly into the results. The deception is effective because this fake content often blends in with the legitimate page, making it difficult for inexperienced users to recognize the scam. It becomes even more convincing when users arrive on the page after clicking what appears to be an official Google ad from the brand.
For example, in Figure 1, we see a Google ad that appears to be for Microsoft tech support. Figure 2 shows what happens after clicking the ad: The user lands on Microsoft 365’s website, but the scammers have manipulated the internal search results to display their fraudulent phone number instead of Microsoft’s real contact details. This same trick has been spotted on other Microsoft pages, like Microsoft Learn, a site that provides training materials.

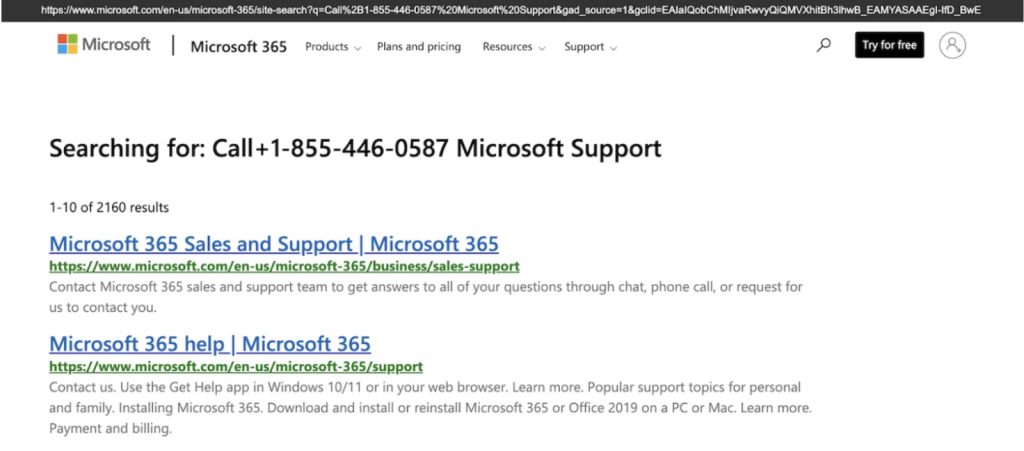
Scammers aren’t limiting this technique to just one brand but they’ve been using it to target multiple companies, including Facebook and eBay. Since we first discovered this attack, Facebook has taken action to protect its website from being exploited in this way.
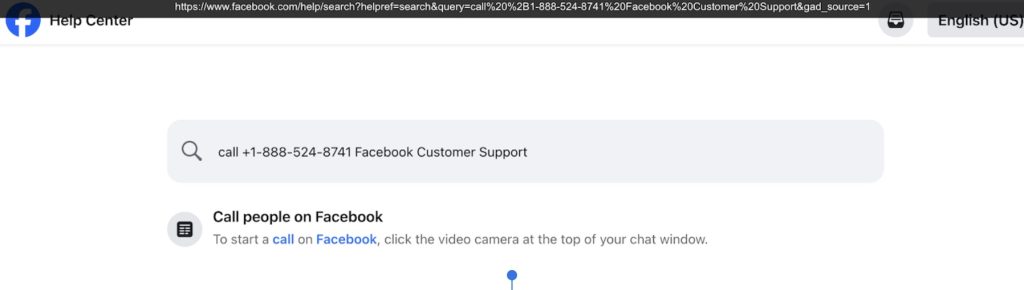
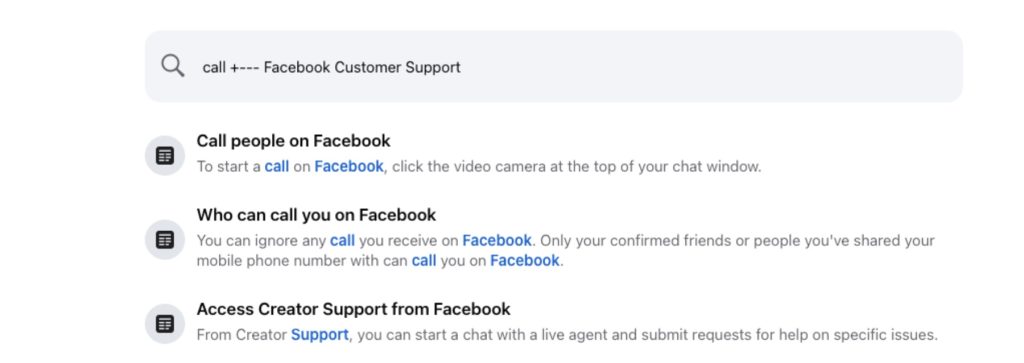
In Figure 3, we see an example of how scammers successfully injected their fake phone number into an internal site search result via a Google ad. In Figure 4, after Facebook’s fix, we can see that the same type of manipulation no longer works. This shows that companies can take steps to close these loopholes, but as long as scammers continue to evolve their tactics, it’s crucial for users to stay vigilant and double-check tech support contact information before calling.
This attack method gives scammers several advantages over traditional malvertising scams that redirect users to fake websites:
-
Lower costs – Unlike conventional scams, this technique doesn’t require scammers to buy domains or rent servers to host fake websites. Their only expense is paying for the ad itself.
-
Harder to detect – Since users are redirected to a legitimate website, traditional security tools struggle to flag these ads. Many detection systems analyze suspicious domains, but in this case, there’s no separate malicious domain—just an ad leading to a real brand’s website. Even if security tools monitor advertisements, they might overlook these because the final destination appears legitimate.
-
More convincing to victims – By injecting fake phone numbers directly into a trusted website’s search results, scammers increase their credibility. Less tech-savvy users are especially at risk, as they may assume the number is legitimate simply because it appears on the official website.
-
Multiple opportunities for abuse – Large companies often operate several portals for different products and services, each with its own internal search function. This gives scammers multiple entry points to exploit.
-
Beyond phone numbers – While phone numbers are the most common type of injected content, scammers could also insert other types of information like fake emails or URLs (unclickable, text-only).
By leveraging these advantages, scammers make their operations cheaper, stealthier, and more effective all while exploiting the trust users have in well-known brands.
Google Support: Suspicious emails or calls claiming to be from Google Ads
Vulnerable Brands among the Fortune 500
We wanted to understand just how widespread this vulnerability is, so we analyzed the internal site search mechanisms of the top 50 US-based companies in the Fortune 500. These include major players across industries such as retail, banking, automotive, and energy.
Our findings were alarming: 86% (43 out of 50) of these companies were vulnerable to this attack, allowing scammers to inject fake phone numbers into their internal search results. Even more concerning, 32 of these websites displayed the injected phone numbers prominently, making it even more likely that unsuspecting users would fall for the scam.
This highlights how widespread the issue is and how urgently companies need to secure their internal search mechanisms to prevent abuse by scammers. We recommend that companies start by identifying all internal site search mechanisms across their websites and portals. Once identified, they should strengthen these systems by improving input sanitization. Specifically, they should detect and remove any injected content such as phone numbers, email addresses, and URLs, which scammers often use to mislead users.
Scam-Related Resource: Global Phishing Scam Hits Canadian Pizza Chains for Credit Card Data





