The US banking industry has seen a significant uptick in cyberattacks, particularly in phishing and spoofing, due to interconnectivity of banks and facilitation of instant transfer, becoming more of a persistent threat. Additionally, the hard hitting attacks in recent times are due to artificially intelligent systems that lead to bot generated spamming. This surge in attacks can taint the reputation of a prominent bank and bring their infrastructure to a halt.
Even governments are taking notice. Recent actions taken by the US Consumer Financial Protection Bureau (CFPB) like the Electronic Fund Transfer Act (Regulation E) are meant to protect consumers from these kinds of attacks and place much of the liability on financial institutions. While this is one example, it highlights the growing focus of concern on consumer-targeted spoofing and impersonation attacks using financial organization’s brands as a vector for fraudulent activity.
Technical Insights On Financial Domain Spoofing Trends Of 2024
Researchers at BforeAI analyzed 62,074 domains registered between January and June 2024 with finance-related keywords. Of those registered domains, 62% (38,737) were found to be involved in phishing attacks targeting legitimate entities via spoofing websites.
Interestingly, well-known financial institutions like BBVA, HSBC, and PayPal were frequent targets which indicates that high profile brands are popular targets for cybercriminals given their growing customer and employee base. In an April report published by Infosecurity Magazine featuring data from security firm Check Point, Wells Fargo was among the top 10 companies to be targeted for scams in the first quarter of 2024.
While brand recognition appears to be a major driver when malicious actors choose spoofing targets, it is less of a blatant risk for smaller firms. Unlike the larger, more prominent financial service firms, smaller businesses with a less recognizable brand presence tend fare better in terms of spoofing because these attempts are more easily detected and addressed, and the potential reach of such an attack is less.
The most commonly-used keywords were related to the financial domain, including but not limited to “money,” “finance,” “fintech,” “cards,” “debit,”, “credit”, and “loan.” These keywords give the domain a more authentic feel, instead of appearing generic or AI generated.
The dramatic rise in spoofing attacks also indicated a pattern in which well-known financial institutions like BBVA, HSBC, and Paypal saw significant phishing threats. This could indicate that high profile financial and banking brands are prime targets for cybercriminals to run their campaigns due to their wide employee and customer base.
Also notable, a variety of online scams were based on “Buy Now Pay Later” (BNPL) offers for cars, phones, and other goods. Major banks like Bankinter, BBVA, HSBC, and PayPal were frequent targets, with over 561 domains associated with each. Another 127 domains used the .finance TLD, although not all were malicious. However, using an industry specific keyword does increase the potential to add credibility to a domain, even though it may be malicious.
Another highly leveraged tactic was to create exact replicas of legitimate organizations with similar names, that can potentially make the victim perceive it to be relevant and sensible. It becomes challenging to distinguish between genuine and fraudulent websites.
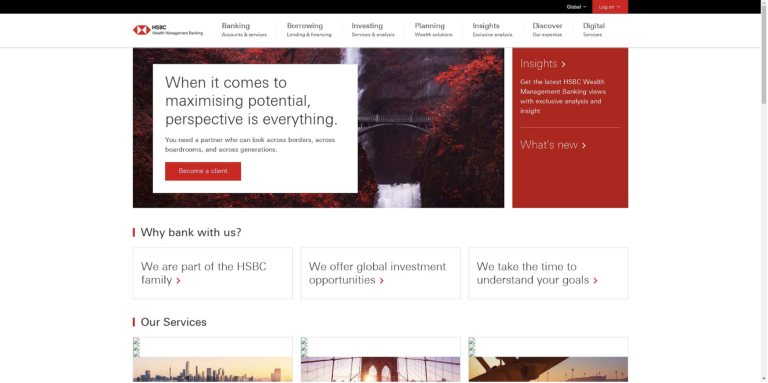
Spoofed domain: hsbcwealthmanagements.com
An additional 185 domains included the word “card” in their URL. Analyzing these domains revealed that a significant number of victims were associated with Sumitomo Mitsui Banking Corporation (SMBC), AEON credit services, and Rakuten. This indicates that financial services providers beyond traditional banks with streamlined business operations are also being actively targeted.
Another group of fraudulent domains focused on exploiting gift cards, particularly for Steam and other gaming platforms. This indicates a section for spoofed websites that offered vouchers or coupons for gaming and entertainment, leading to financial losses.
Spoofing: A lethal concept backed by AI
Spoofing and phishing tactics are becoming increasingly advanced due to AI technology that enables execution on a larger scale and while remaining undetected for longer periods of time. With billions of phishing emails sent every day, countless spamming websites are hosted for the express purpose of receiving redirected victims to harvest and compromise their data. This leads to the generation of multiple newly registered domains (NRDs) on a daily basis, most of which are likely AI-generated.
The ease of access to phishing kits and the increasing sophistication of spoofing techniques have contributed to the rise in these attacks. By leveraging AI-generated deepfakes and other advanced templates, attackers can create highly convincing phishing campaigns that can deceive even the most vigilant users.
Technical aspects such as Natural Language Processing (NLPs), Machine Learning, and Deep Learning are crucial in creating personalized spoofs and dodging newer detection methods. Over time, as AI learns the patterns of spoof generation, it tends to get even more sophisticated, making it impossible to identify legitimate and synthetic communications.
While not a financial service firm, the sophistication of the recent Pepco incident is a wake up call highlighting the need for AI-based defenses to match AI-based threats. Discovered in February 2024, the Pepco BEC scam is a leading example of spoofing backed by state-of-the-art AI technology being used to spoof employee email addresses and target the accounting department to send urgent invoices. This attack led to a loss of approximately €15.5 million cash for Pepco.
Impact
The repercussions of a sophisticated spoofing attack can cause damage beyond individual victims and financial losses. With every spoofed indication observed for a bank or financial institution, it represents a direct hit to the brand’s credibility as its ability to safeguard itself can be called into question.
What’s more, in the case of consequent targeted attacks, the brand can receive negative publicity in the media, impacting the future relations with the customers and investors in the market.
From a technical standpoint, a spoofing attack ignites a chain of future malicious attacks. Some examples include malware and ransomware delivery through spoofed applications and websites. Rewards and cash-based attacks can lure victims to provide OTP (One Time Passwords) to the attackers in real time, enabling the risks of account takeovers and fraudulent transactions. Cybercriminal forums often discuss different banks and their methods to perform carding attacks, which includes gathering CVVs and CVCs to perform unauthorized transfers.
Mitigation
It has become a “must” for financial organizations to protect their consumers and employees from falling victim to financial spoofing fraud. Protective measures such as verifying redirections from any SMS text or email and checking for any warning signs on the webpage is unavoidable. Consumers need to focus on cyber hygiene practices such as regular changing of passwords, and use of Multi Factor Authentication (MFA). If one suspects they are victims of compromise, it is advised to immediately alert the respective bank and monitor for any unauthorized transactions. Having a layered approach in cybersecurity can be beneficial in minimizing the risk of financial fraud.
Financial industries and banks should focus on adopting predictive security solutions
and early threat indicators along with their existing infrastructure. The use of AI in anticipating threats can accelerate the organizations towards cyber deterrence based on historical patterns, and should be prioritized as soon as possible. Regular threat monitoring combined with new AI-based solutions provides a multilayered approach for mitigations before they turn into a costly incident.
Conclusion
The spoofing trends of the financial domain in 2024 continue to escalate, affecting businesses, individuals, and employees. This can result in loss of finances, and affects brand reputation, customer trust, and the security posture of financial organizations.
The reason for the rise in spoofing attacks is the ease and accessibility of phishing kits, either from publicly available sources or paid “Phishing-as-a-Service” (PhaaS) solutions. Moreover, the emergence of deepfake technology enables criminals to circumvent the eKYC and create fake accounts.
Predictive security that leads to cyber deterrence can effectively mitigate threats rising from spoofing. Thus, seeking solutions that largely focus on providing insights into the future threat landscape is essential.