Overview
This report investigates a phishing campaign targeting various government agencies and services, specifically focusing on toll road payment systems such as TxTag, a toll road maintenance provider local to the state of Texas and other states around the US. The campaign employs typosquatted domains and malicious SMS phishing (smishing) tactics to deceive users into divulging sensitive information, often leading to financial fraud.
Phishing Tactic Observed
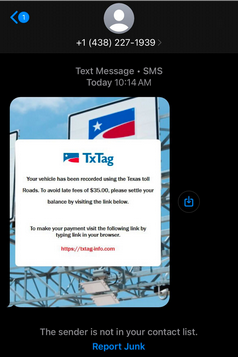
The campaign begins with the threat actor sending fraudulent SMS messages to unsuspecting users, claiming unpaid toll fees. The message includes a link redirecting the user to fake websites designed to mimic official tolling agencies like TxTag.
The phishing domains used feature slightly altered versions of legitimate domains to increase credibility. For example, we observed the phished version of the legitimate domain of TxTag (txtag.org), to be txtag-info.com.
Infrastructure Details
This domain, observed on IP address 104.252.127.23, belongs to IP address 104.252.127.0/24 and is associated with a high concentration of various cybercrime infrastructures. The ASN of the domains is 56971, belonging to CGI Global Limited, the hosting provider for these domains. This provider has a history of hosting questionable or malicious content. This SN also has multiple malicious domains observed targeting toll systems operators, as well as utility companies and unrelated sectors.
Key Findings
Domains Identified
The identified domains add 40 entries, expanding our investigation across 6 U.S. states (VA, KS, NH, IL, FL, OH). This indicates an evolving targeting model focused on regional toll systems and their customers, making monitoring crucial. Some of them include:
- Toll and Transport Services:
- txtag-info.com (TxTag)
- ntta-info.com (North Texas Tollway Authority)
- toll-ntta.com (North Texas Tollway Authority)
Indicators of Compromise (IOCs)
The following IOCs are critical for network defense and blocklisting:
IP Address | IP Address | ||
104.252.127.23 | 82.147.88.22 | ||
Domains | Domains | ||
txtag-info.com | toll-ntta.com | ks-lanes.com | pass-fl.com |
ntta-info.com | nh-pass.com | https.va-route.com | va-toll.com |
coned-ny.com | ohezp.com | ezpoh.com | va-road.com |
igetpaidtotrade.com | ntta-pay.com | va-lane.com | fl-road.com |
sinocompass.net | iltway.com | ks-drive.com | va-ez.com |
ygncgk.top | toll-tx.com | iltolls.com | |
ilroad.com | ezp-va.com | ||
va-route.com | toll-va.com | ||
Insights into threat actor’s motives and techniques
While the primary focus appears to target toll and utility payment systems, the inclusion of unrelated domains like igetpaidtotrade.com suggests the actor may be conducting diverse scams under a unified infrastructure. The main motivation of the actor is to likely conduct financial fraud by spamming a large number of recipients in the hope that some fall for the scam. US-based toll systems seem to be the prime targets (e.g., TxTag and NTTA), indicating a focus on U.S.-based victims.
Detection trends
Detecting these campaigns can be accomplished through analysis of SMS phishing (smishing) instances that target victims using unpaid tolls as a context. Phrases such as, “Your toll fees are unpaid” and “Click here to pay now” are used by the criminals to create a sense of urgency. By using different alphanumeric variations of the legitimate websites, like replacing ‘o’ with ‘0’, or using hyphens (txtag-info.com) and subdomains of generic websites (link.ohezp.com), the criminals attempt to create visually similar URLs to real platforms. Additionally, the use of recently-registered free SSL certificates aids to enhance the website’s perceived legitimacy.
Conclusion
This phishing campaign highlights the evolving tactics used by cybercriminals to exploit public trust in government and utility services. Through the combined use of typosquatting and SMS phishing, the actors aim to harvest sensitive information or conduct financial fraud. This highlights the importance of close collaboration between cybersecurity teams, hosting providers, and law enforcement to dismantle these operations.
As for drivers in the area where these toll tag scams are frequent, be wary of emails and messages received from random accounts. All tag-related information should be accessed on official, government-approved websites. Be sure to report suspicious domains to your ISP or national cyber security forums and block all communication from the scam accounts to prevent future scams or accidental interactions.
Since such scams are widely seen on mobile devices or SMS texting, consumers should install strong anti-virus apps to protect from malware infection.