Natural disasters like the Los Angeles wildfires of 2025 often create an opportunity for cybercriminals to exploit the vulnerabilities of human psychology. Researchers at BforeAI discovered multiple threats surrounding the recent natural calamity in Los Angeles, California. These threats involve multiple phishing campaigns centered around various themes such as insurance, fundraising, claims, restorations, and the fire department.
To maintain the relevance of the campaign, keywords such as “support”, “la”, “fire” were observed in most of the domains retrieved since the incident. This report examines the patterns of domain registrations related to the LA wildfires, identifying trends and potential risks.
Domain Trends
The analysis includes 119 domains registered between January 8, 2025, and January 13, 2025, across various registrars. The domains primarily target keywords such as “LA fire,” “wildfire,” “relief,” “fund,” and “rebuild,” indicating the keyword relevance with the wildfire disaster. All the domains were registered in a short frame of time once the incidents started gaining significant coverage in the media and sympathetic responses from people around the world.
Interestingly, 58% of the domains were registered through GoDaddy, making it the most commonly used registrar in this campaign, followed by Namecheap and Register. Other prominent domain registrars included Ionos, Hostinger, Squarespace, Tucows, etc.
The most prevalent top level domain (TLD) was “.com”, accounting for 70% of total count, followed by “.org”, and “.net”. Some of the domains also used “.fund” TLD, hinting at a relevance to a financially fraudulent campaign, while others attempted to establish credibility of the domain by using popular TLDs.
| Theme | Examples | Observation |
| Emergency assistance and relief | helplafire[.]com, fundlafires[.]com, lafirevictimsnextsteps[.]com | Likely to cause financial losses and harvesting of PII. |
| Legal and insurance services | lafireinsuranceclaims[.]com, lawildfiresclaim[.]com | Might host potential phishing targeting wildfire victims seeking compensation. |
| Cleanup and reconstruction services | lafirecleanupcrew[.]com, losangelesrebuild[.] com | Might establish fake businesses to conduct financial scams. |
Phishing trends surrounding the Los Angeles wildfires
GoFundMe campaigns
Some of the domains target human emotions and triggers, such as (e.g., “findmypetlafires[.]com,” “helplafire[.]com”) and financial recovery efforts (e.g., “lafireinsuranceclaims[.]com,” “lafirelegalhelp[.]com”). Following this, various pet-based fundraisers were promoted on social media and websites, which used pictures from previous tragic incidents and thereby hosting a fake gofundme campaign.
For example, a person created a GoFundMe for a dog, titled as, “Aid Our Recovery from LA Fire Tragedy” (www.gofundme[.]com/f/aid-our-recovery-from-la-fire-tragedy), by using a picture of another alleged scam campaign of a cancer stricken dog.

Similarly, another instance of a GoFundMe for a horse, titled as “LA Fire Relief for Vulnerable Animals” (gofundme[.]com/f/la-fire-relief-for-vulnerable-animals), but the image the creator copied from the tragedy happened in November of 2024, before the LA fires ignited.
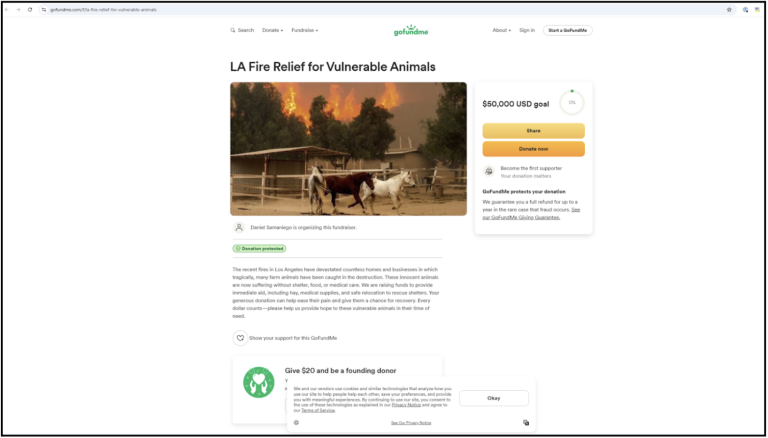
We identified at least 8 fraudulent GoFundMe campaigns, which were deceptive, money-driven schemes created by reusing old images.
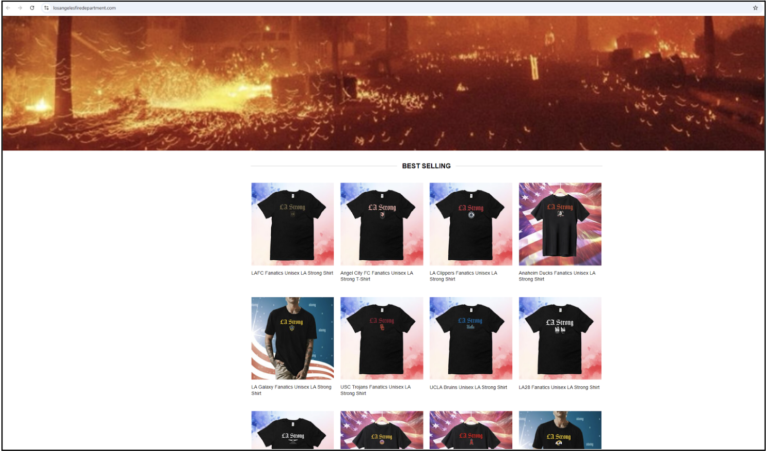
Merchandise Store
Some websites were found to be running apparel and merchandise stores in the name of the LA fires incident. This website was running under the name ‘Los Angeles Fire Department’.
LA wildfire themed cryptocurrency
Various cryptocurrency platforms are experiencing a surge in new coins following this incident. While their legitimacy is unverified at the moment, traders fall prey to ‘get-rich-quick’ scams.
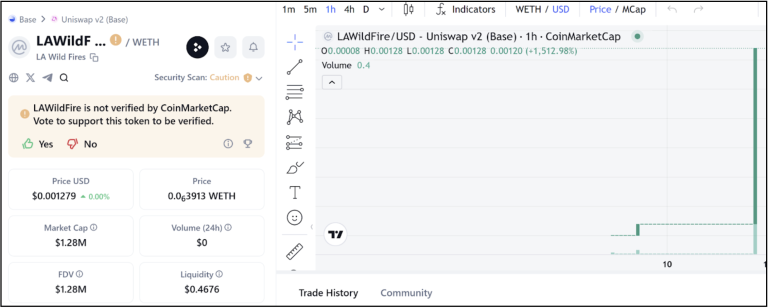
Another website was preparing to launch its cryptocoin shortly after the tragic incident. Individuals who faced heavy asset losses in this incident might be potentially vulnerable. These “pump and dump” schemes frequently leverage social media platforms to reach large audiences, making malicious crypto campaigns successful.

Impact | Mitigation |
|
|
Context: How does this scam activity compare with other natural disaster activity?
Hurricane Helene vs. LA Wildfires Comparison
Event Characteristics | Hurricane Helene | LA Wildfire |
Predictability | Hurricanes are often tracked days or weeks in advance, allowing scammers to register domains proactively. | Wildfires can ignite and spread unpredictably, leading to more reactive domain registrations. |
Relief & Rescue Focus | Malicious infrastructure often focuses on disaster relief donations, emergency shelters, or fraudulent weather updates. | Scammers target affected areas directly, focusing on local support, donations, or updates. |
Geography | Impact spreads across multiple states or countries, broadening the victim pool. | Malicious domains may exploit air quality alerts, medical aid for respiratory issues, or evacuation notices. |
Target Audience | Broader demographic including international audiences concerned about affected regions. | Local business and populations in California and nearby states. |
Scam Domain Themes |
|
|
While both Hurricane Helene and the LA wildfires led to an increase in malicious domain activity, their nature dictates different strategies. Hurricanes lead to broader, premeditated scams with global appeal, whereas wildfires drive hyper-local, urgent, and reactive scams that prey on fear and immediate needs. It is interesting to note that both disasters saw crypto related scams.
Appendix:
[1] Indicators of Future Attack (IOFA) list.
Media Contact
Andy Tzortzinis
Director of Brand and Product Marketing
BforeAI
[email protected]