The tax season is upon us, and while this tends to be a profitable time for financial consultants and tax advisors, there are others making a profit, as well: Cybercriminals! Research at BforeAI indicates a notable rise in malicious activity related to tax and refunding over the past six months. BforeAI threat researchers have observed the usual phishing techniques such as typosquats of the word “refund” (e.g., “refound”) for detection evasion, or following a particular pattern of numbers concatenated by ‘refund’ strings. Domains such as these rose to as high as 345 subdomains being registered in the past month. Additionally, numerous phished websites used government based themes to trick individuals into believing they are on legitimate tax filing sites.
That said, this tax season, as we pay our due, we should also be on the lookout for potential scams. Likewise, organizations that support tax operations, such as certified public accountants (CPAs), financial advisors, banks, employers, investment funds, lenders, and tax preparation software companies should also move to protect their customers and users from these crimes. Lets uncover some unique scam instances that the BforeAI team encountered.
Note: This report primarily focuses on IRS (Internal Revenue Service)-related scams in the United States, however every country with a tax code requiring citizens and residents to report taxes owed is susceptible to these types of scams.
IRS Threat Report
Old domains being resurrected for new campaign themes
The threat research team observed old domains, registered as far back as in 2009, were re-registered in December of last year (2024), right before the tax season. Due to successful evasion techniques used by these cybercriminals, old websites with good reputations and rankings on search engines garner a sense of legitimacy among the targeted audience. Since security analysts generally warn people interacting with recently registered websites, old websites remain off the radar.
Several websites registered using freely available platforms such as the popular blogging site, “blogspot.com” (Figure 1). These fraudulent sites feature attempts to make use of every possible opportunity to ensure the visitor believes that an alleged “warning” was waiting for them. However certain blunders on the website such as misplaced punctuation, informal abbreviation such as ‘pls’, use of emojis, inconsistent spacing, and more, were common.
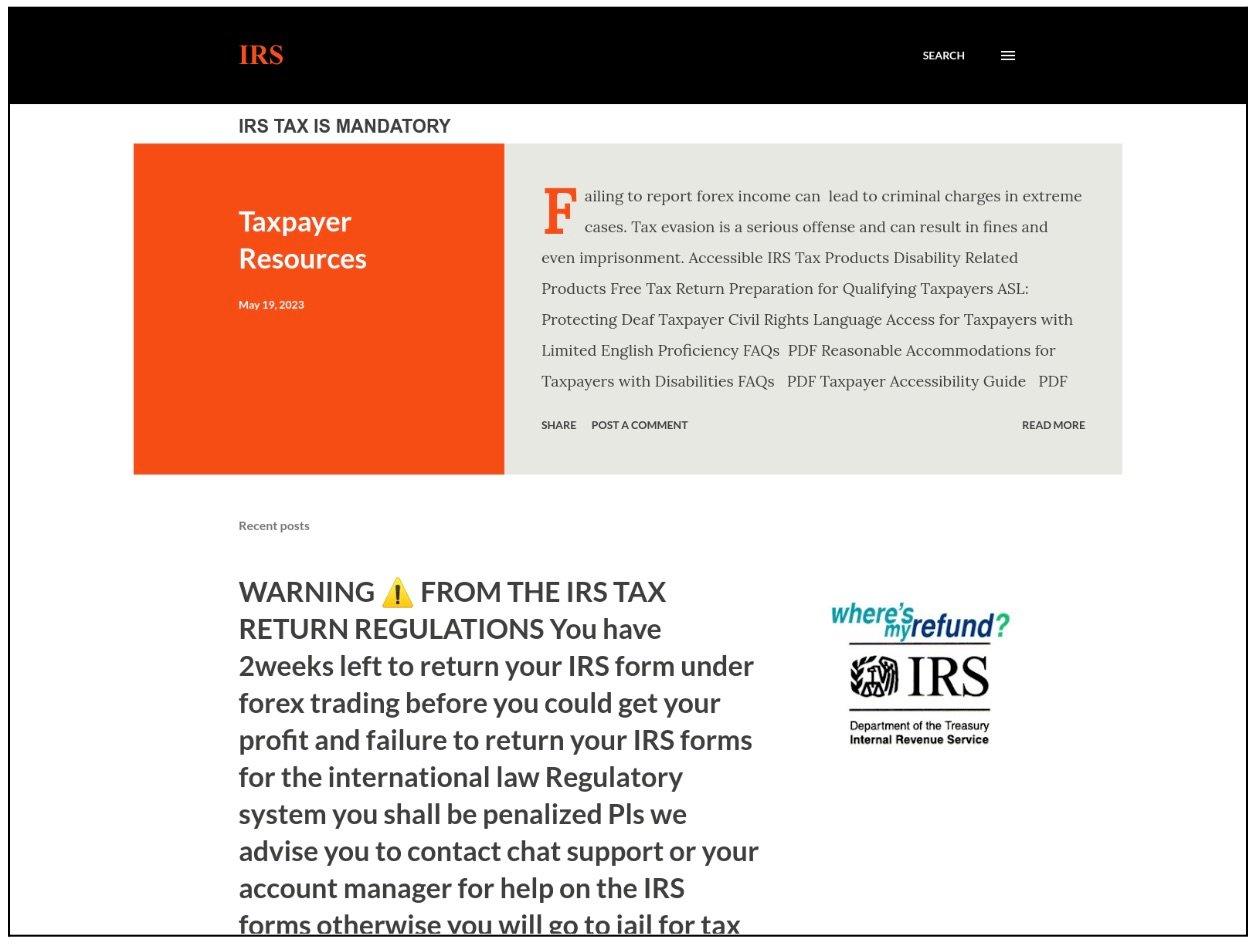
Figure 1: Scammers using a fake notice on popular free blog hosting platforms
A network of 345 subdomains hosted on Cowboy servers, offered purportedly “free” tax filing services while falsely claiming support from the U.S. Department of Treasury. All of these subdomains followed a unique pattern of pr-[random four numbers][.]getyourrefund-testing[.]org (Figure 2).
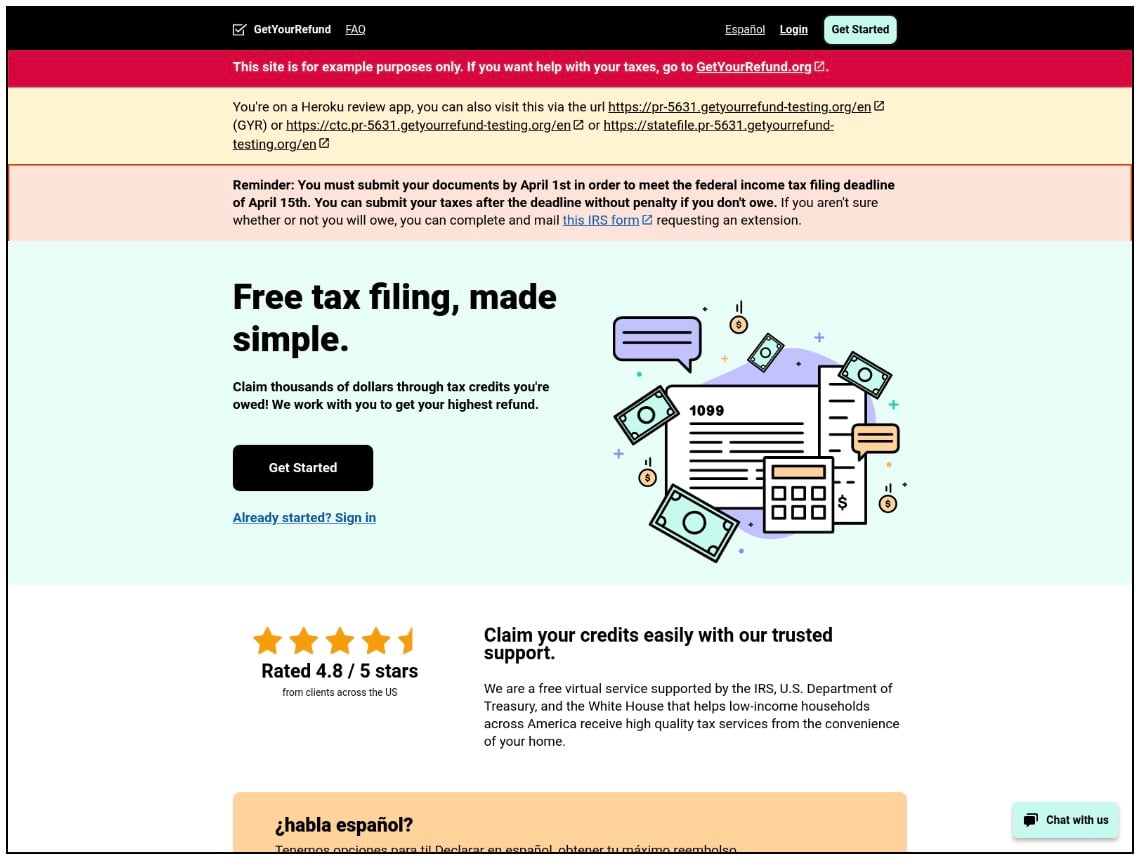
Figure 2: Illustration for the sample of the official Get Your Refund website.
While the website itself appeared to be a Heroku-hosted template, the fact that 345 related sites were recently updated, strongly suggests that victims could be defrauded in the process.
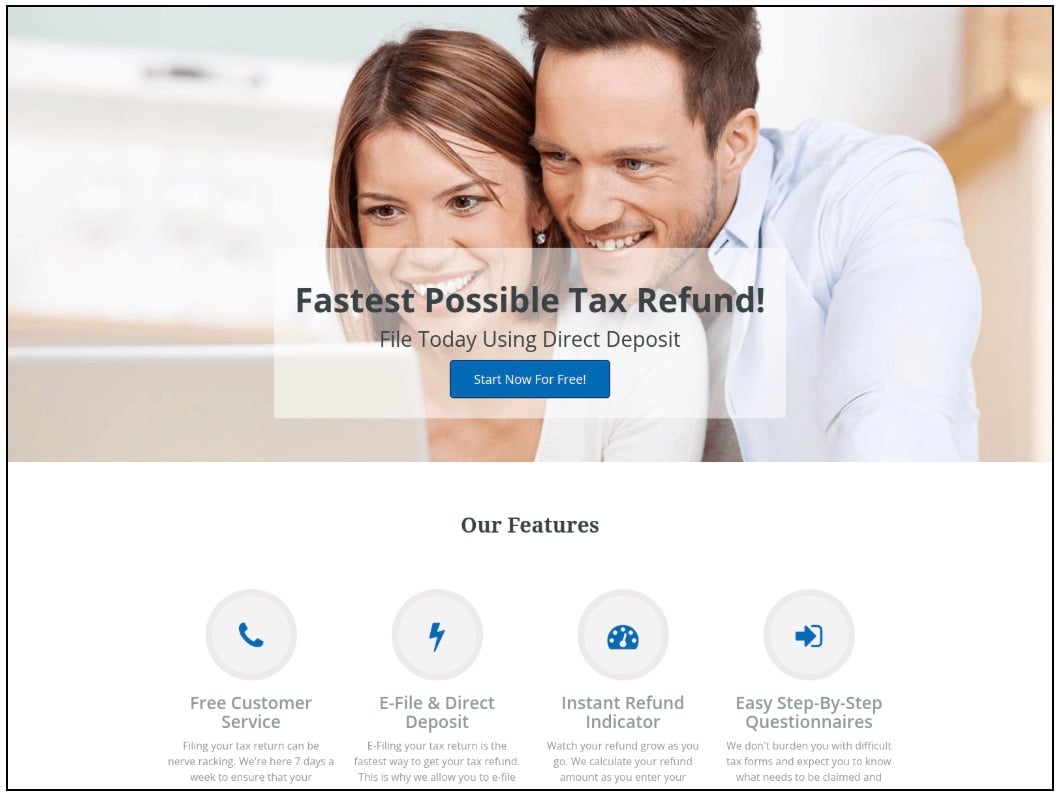
Figure 3: Various tax companies are emerging with phished templates resembling legitimate sites and utilizing page title stuffing methods
Numerous template websites emerged strategically using keywords relevant to tax filings. One such example mentioned above (Figure 3), presents itself as a legitimate tax service, despite lacking verification. However, these websites used, “tax return”, “tax refund”, “IRS”, “taxes”, “e-file”, “income tax”, and “efile” all crammed together in the page title.
Stuffing keywords in page titles is an unsavory, yet popular search engine optimization tactic used by threat actors to artificially boost their search rankings. Sometimes this can lead to outranking of popular businesses in the same avenue. However, there is a psychological tendency for a user to click on the top search result when conducting a search, so negative tactics like this result in malicious websites receiving the traffic, ultimately leading to successful phishing and tax fraud.

Figure 4: Website using keywords concatenation of Trump with tax keywords to engage the U.S. audience
Leveraging the current political climate in the U.S., cybercriminals launched websites mentioning President Donald Trump along with tax-related keywords to attract users to their alleged services. For example, one website used the keyword “trump” with “tax refund” while also provisioning a tax calculator (Figure 4).
Beyond traditional tax scams, the team also observed cybercriminals venturing into the cryptocurrency space, specifically in the form of meme coins schemes. In one example, a “No Tax Coin” featuring President Trump was observed (Figure 5). Others, while being particularly poorly created examples, mentioned the IRS along with gibberish data. The fact that both these sites were registered within the same month in early 2025, indicates the willingness of cybercriminals to pivot into other avenues of crime, including cryptocurrency scams.
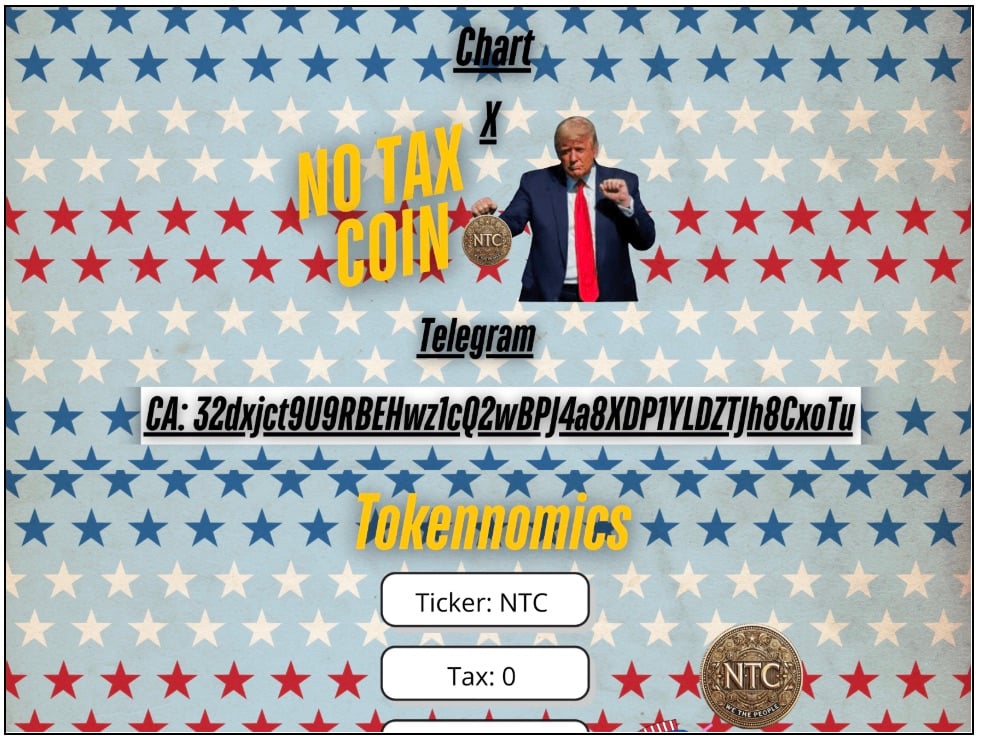
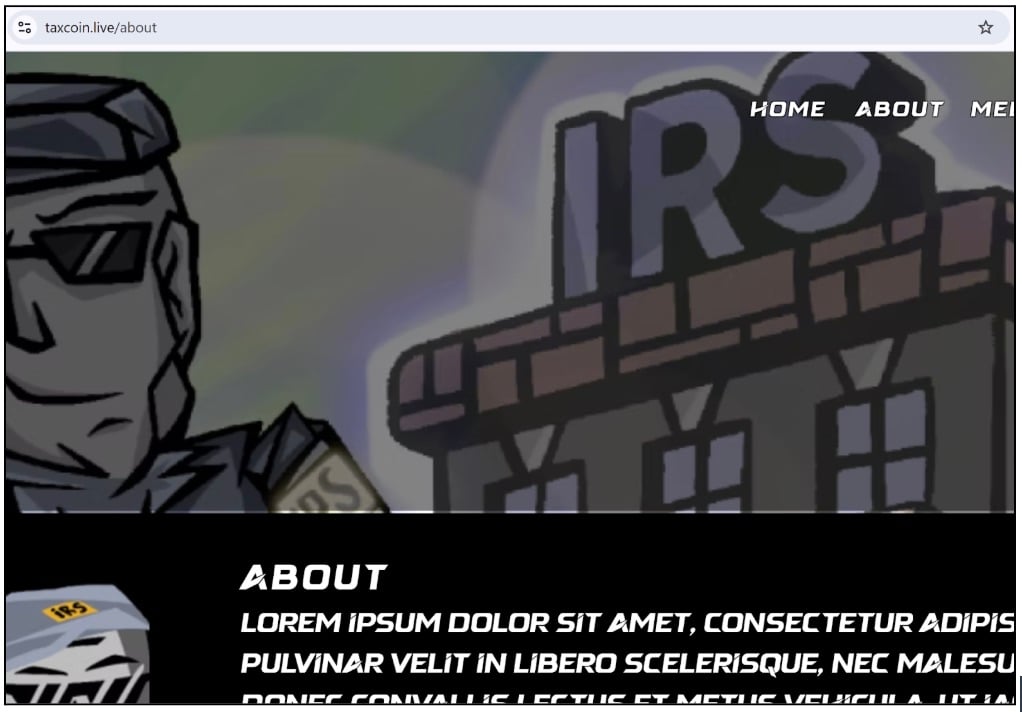
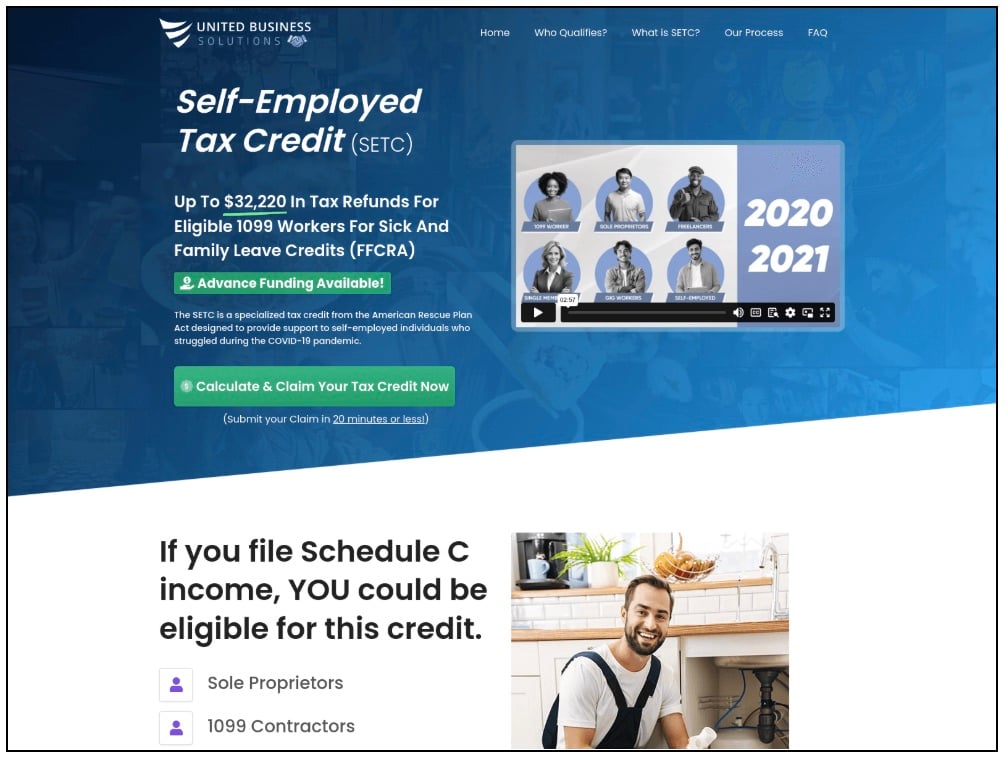

Figure 5: Tax based coins featured live in early 2025, leading to financial frauds in the volatile crypto avenue
The team identified a new tax-related service in which recently established businesses are leveraging the “gov” keyword to gain trust and mislead people in search of legitimate government services. One such website, which previously advertised a service to claim up to $32,000 in just 20 minutes, now features an affiliate/referral link and promotes a completely different business offering.
Various websites using the official logo of the United States Internal Revenue Service (IRS)
Another malicious tactic observed several times was the use of the IRS logo to make fraudulent websites mimic the official website. The threat actors strategically blended the colors of the original websites, however the use of different fonts created a confusing and unclear target audience.
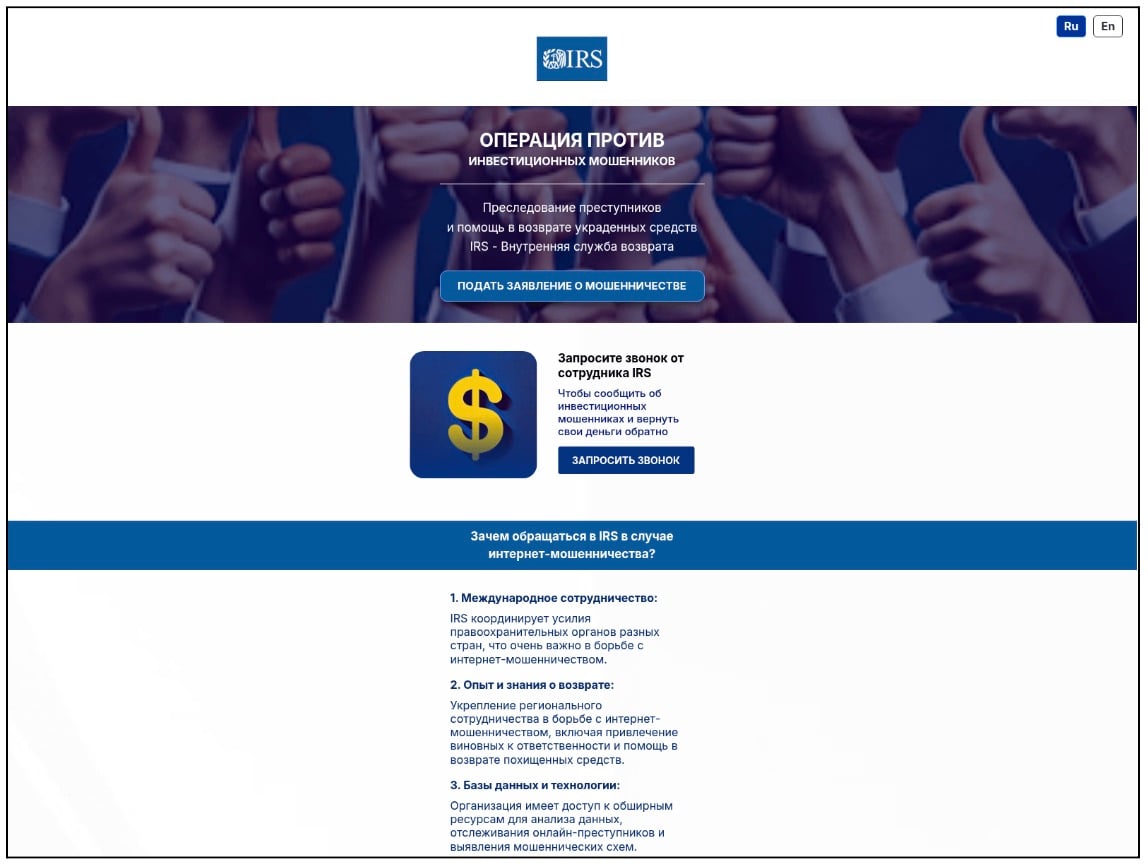
Figure 6: This particular site used the official IRS logo but is in Russian language as is likely targeting Russian nationals
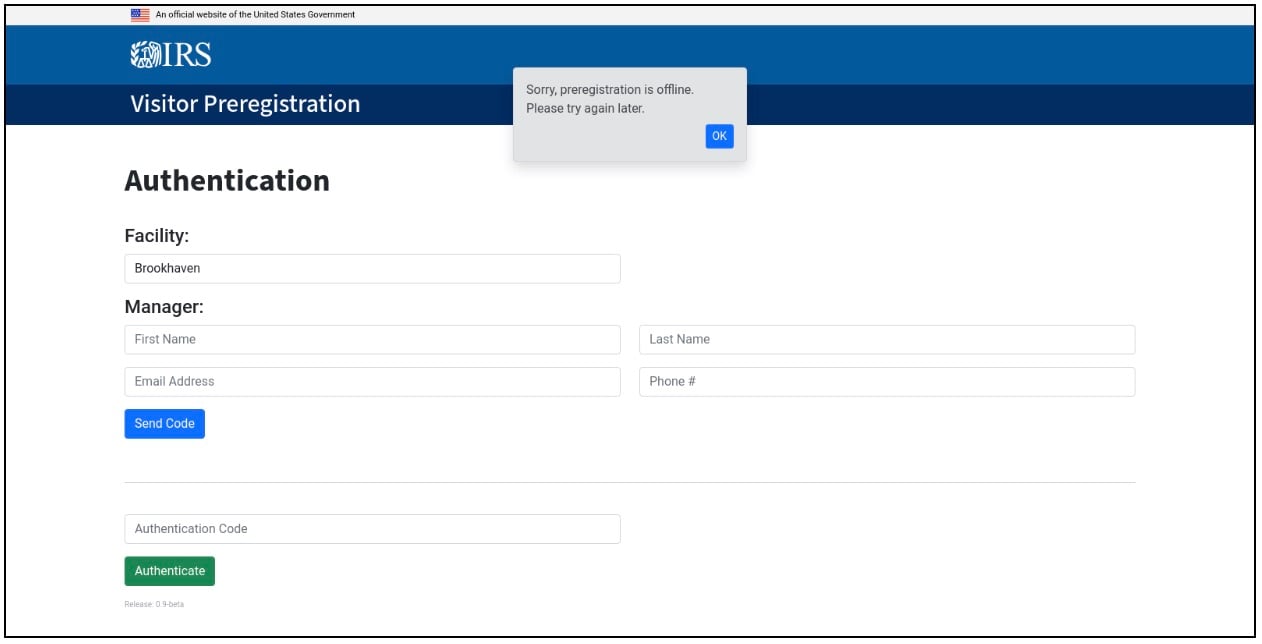
Figure 7: Preregistration technique deployment
While using the official website content of the IRS, this website (Figure 7) is enabling authentication for managers of the IRS Department, likely to steal credentials. These details can be further propagated for social engineering purposes, with the attackers impersonating IRS officials. Although the site’s content is currently unavailable, its prior activity indicates a clear and present danger.
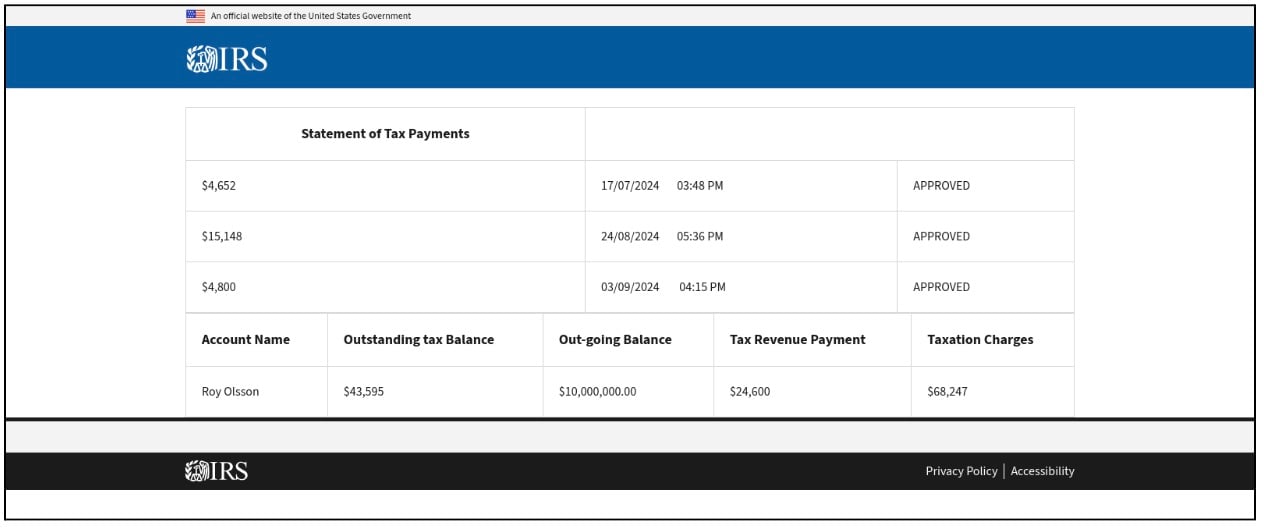
Figure 8: Tax statements leading victims towards financial fraud
Certain websites displayed statements of tax payments (Figure 8), and the purpose of this display remains uncertain along with the methods used to commit the actual frauds. However, there is a possibility of luring victims into checking their statements, and thereby giving up their financial data.
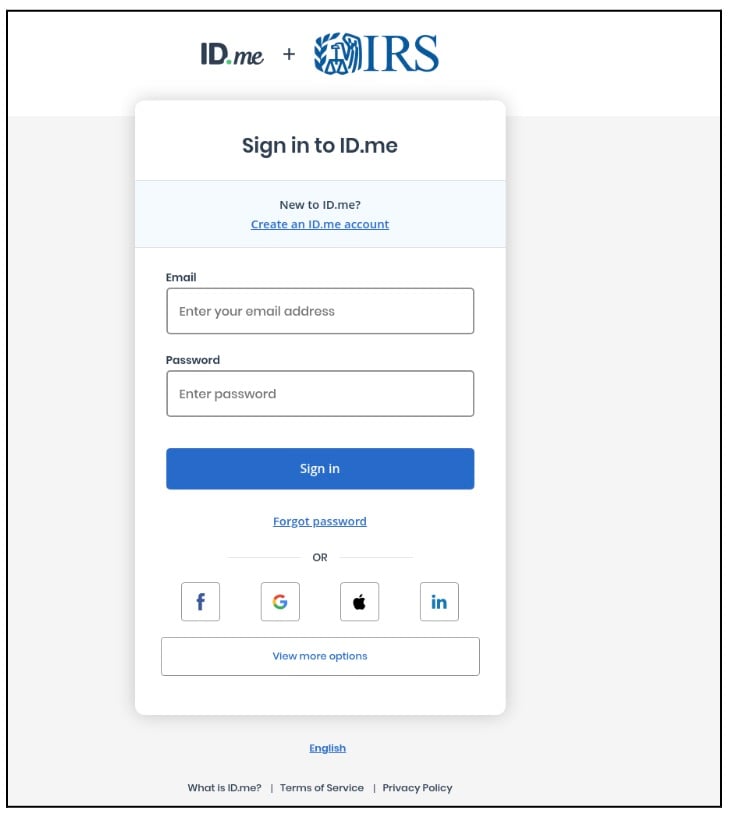
Figure 9: Attempts to harvest credentials propagating t IRS schemes
The team also observed standard phishing attempts featuring fake login and signup forms requiring users to authenticate via ID.me, Google, or other social media accounts (Figure 9). This tactic is a typical data harvesting technique used to obtain credentials during the tax season to commit tax fraud.
The team encountered a case in which, despite having altered content due to the cybercriminals’ quick pivot, still contained IRS-related elements in its page source (Figure 10). In this particular example, this site impersonated the login page of the University of Leeds, where victims were prompted to enter sensitive information, including their social security number and driver’s license. This phished fake is being hosted on pages[.] dev, a classic tactic to host different pivoting methods on free hosting sites.
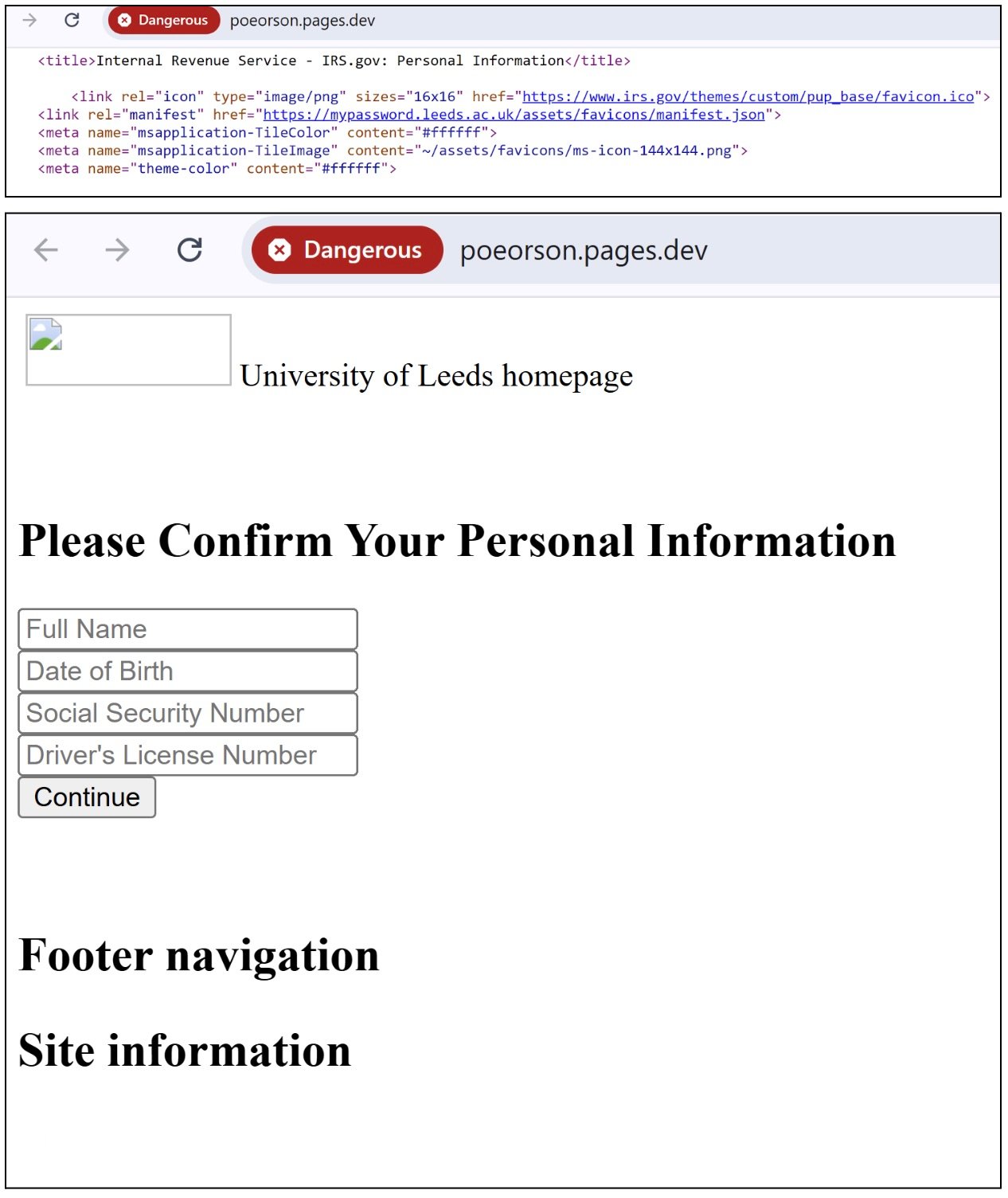
Figure 10

Figure 11
One website (Figure 11) offered up to $1400 USD under the Economic Impact Payment, promising to send the money within 1-2 business days. However, these “get rich quick” schemes often trick people into believing they can easily make money by sharing personal details, only to receive nothing in return.
The team identified over 600 such websites that were a combination of both, using the logo of the IRS and using page title as “Internal Revenue Service | An official website of the United States Government”.
Conclusion
As we fulfill our tax obligations this season, be on the lookout for tax-related traps laid by cybercriminals. The examples covered in this report provide examples of different types of cybercrime, and users should understand the critical importance of verifying website URLs, refraining from quick money schemes, and only engaging with official government websites.