Researchers at BforeAI observed a recent surge in phishing attacks leveraging alleged communications from the Dubai Police, an integral part of the government of Dubai, and a frequent target of cybercriminals. This campaign is primarily being relayed via SMS (Short Message Service) texts in which URLs are attached to redirect users to a malicious domain. Our analysis of 268 domains was based on keyword matches over the time period spanning 17 September 2024 through 22 November 2024 to uncover specific patterns and trends involving the mention of Dubai Police.
Domain-based trends
Related domains have been registered in sequential order, such as “domain-name1”, followed by subsequent numbers, indicating use of an automated domain generation algorithm (DGA) or bulk registration. Generally, typosquatted domains were observed with various misspellings or slight variations of “Dubai Police”, such as “dubaiploce”, “dubaipoqce”, “dubaipoiqt” (see Figure 1). Additionally, terms like “police,” “gov,” “portal,” and “online” were added as suffixes to add legitimacy and relevance, with the goal of building trust among users visiting the domains. This deliberate attempt to impersonate legitimate government and law enforcement services was done with the intent to commit financial fraud targeting average citizens and residents from UAE (United Arab Emirates).
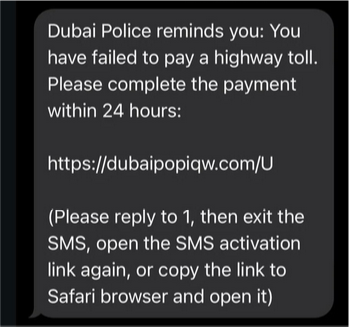
Figure 1
Our researchers observed additional supporting keywords such as “verify”, “gov”, “onlineportal”, and “govservices”, as well as the use of emergency numbers like 999 (the local number to contact emergency services). This is likely intended for individuals who are “fined” as a part of the campaign or citizens who are looking for legitimate emergency services from Dubai Police.
Apart from the main top level domain (TLD), “.com”, there was also heavy use of less-regulated TLDs such as “.top”, “.xyz”, “.icu”, “.buzz”, “.click”, and “.one”. The TLD distribution is as follows:
| TLD Distribution of Phishing Domains Targeting Dubai Police | |
| com | 151 |
| icu | 6 |
| xyz | 9 |
| top | 49 |
| cc | 13 |
| life | 1 |
| one | 4 |
| click | 5 |
| fun | 19 |
| shop | 1 |
| fr | 1 |
| buzz | 2 |
| link | 3 |
| help | 1 |
| co.in | 1 |
| online | 1 |
| info | 1 |
Whois-based trends
Most of the domains originated from Tencent servers based in Singapore, which have a history of malicious activity including spam, phishing, and botnets. Approximately 50% of the domains were registered by Gname, followed by NameSilo, and Dominet.
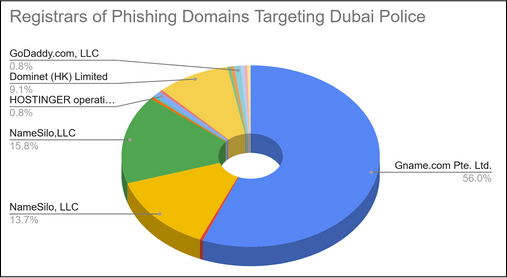
Out of these domains, 26 have already expired, with some of them being registered as recently as November 2024, indicating the short life of these campaigns. These short-lived campaigns are intentionally brief, so the threat actors can move on to the next campaign..
Two of the registrants were found to be from India and Dubai itself, with suspicious names suggesting that they originate from a legitimate company. In other cases, the threat actors have managed to keep their identity anonymous.
Mitigation for citizens and residents of UAE:
- Always double check the official domain of the Dubai government and the payment portal before proceeding with any payment. The correct home page website for Dubai Police is: https://www.dubaipolice.gov.ae/wps/portal/home
- All calls and notifications from unrecognized and apparently “new” services pretending to be from the government should be avoided and alerted to internet service provider (ISP) phishing reporting websites such as Etisalat and DU.
- Stay cautious of websites that are missing “HTTPs” protocol, broken links, out of place web designs, or content with a suspicious or shady tone. If it seems “off”, it probably is!