.png)
Citizens Financial Group, Inc. is an American bank headquartered in Providence, Rhode Island, which operates in 14 U.S. states.
During our PreCrime internet scout of December 12th 2022 we identified suspicious markers across multiple vectors. One of those was this website spoof that could be targeting unsuspecting users of Citizens Bank.
The Attack
Legitimate site :
citizensbankonline[.]com
Malicious domain created on December 12, 2022, identified by Bfore.Ai on December 13, 2022
ctyvs[.]link
This attack shows a brand impersonation attack on Citizens Bank, an American Bank operating in 14 U.S. states.
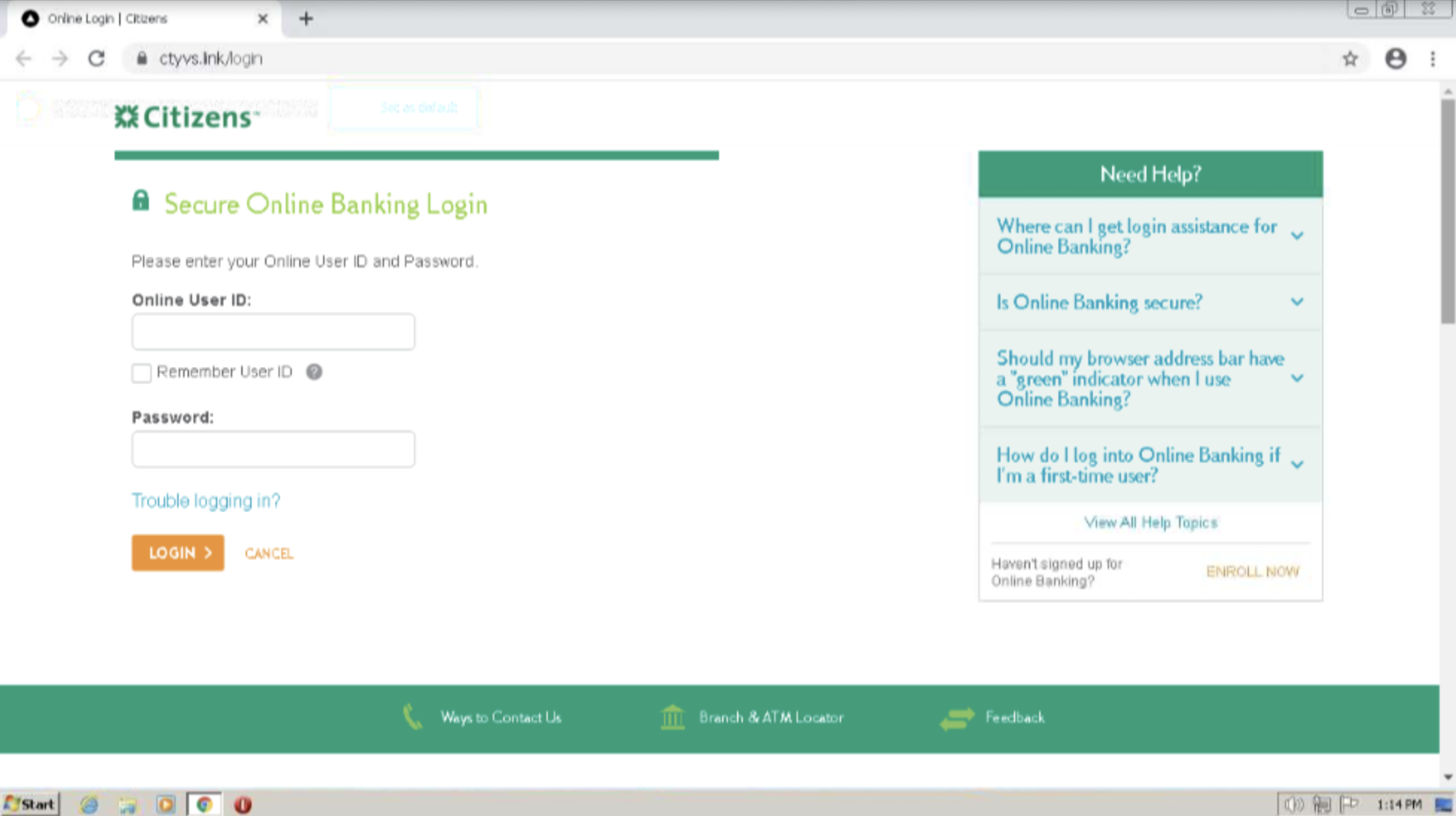
Malicious site

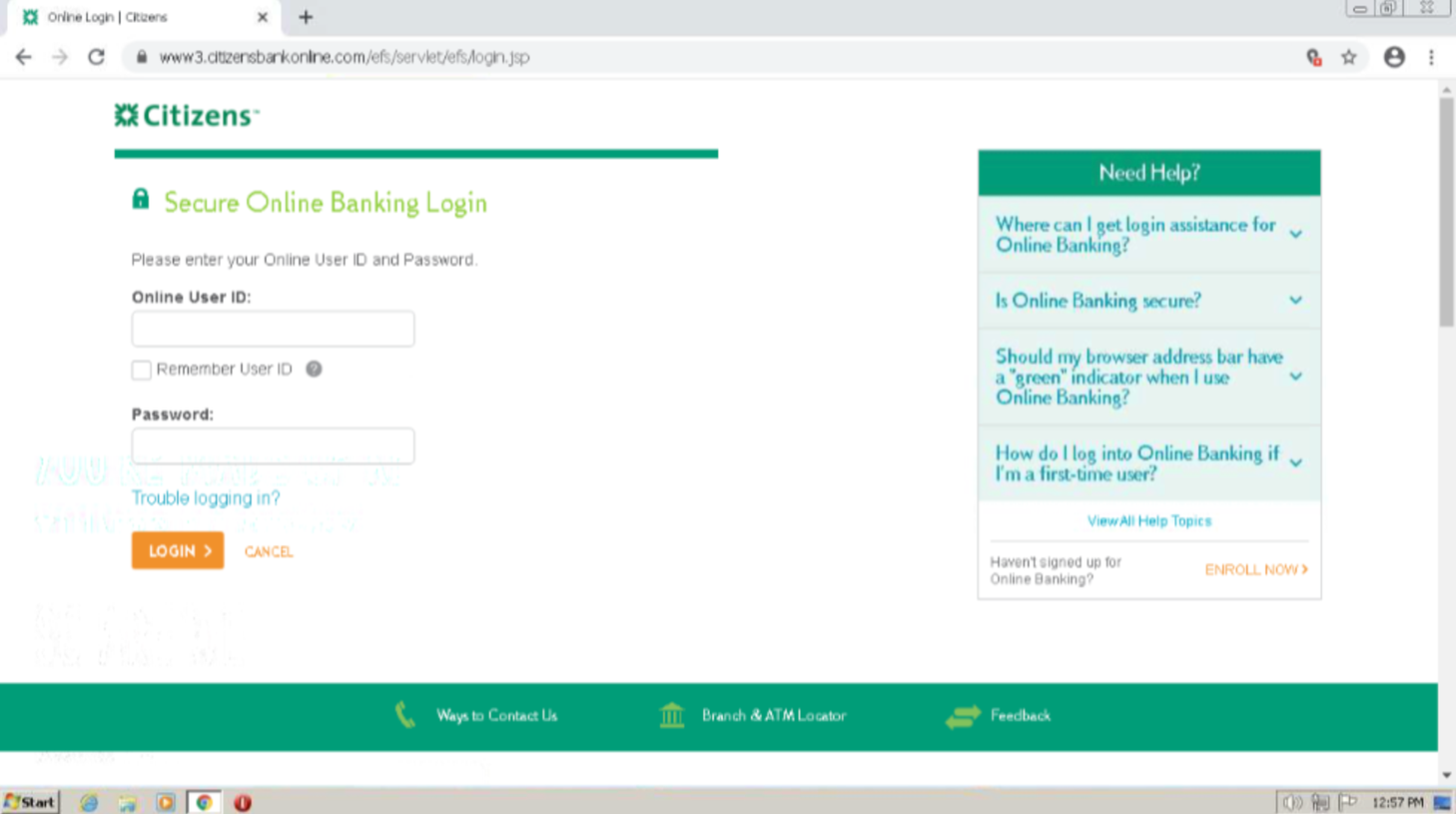
Legitimate site
How does this attack work ?
-
The URL leads users to a clone of the legitimate sites login website, where they are asked to login to their Citizens Bank account.
-
Once a user has logged in, they are asked to complete 6 steps to “secure your account“ as it is “currently on hold”. Through these 6 steps users are asked to reveal personal sensitive information including, choosing and answering 5 password questions such as, what was the name of your high school?, credit card number, expiry date, CVV and ATM pin.
How do they trick users into believing the attack is real?
-
Users may be led to the malicious website through a phishing campaign, wherein they are asked to go to the website in order to verify their account due an issue. The threat actors will likely attempt to convince users that this is an urgent matter, a tactic often used to make victims feel a sense of urgency and thereby more likely to comply.
-
Using branding from Citizens Bank including the same logo, colours and font. Additionally, the malicious login page is completely identical to the legitimate one in appearance.
-
By showcasing legitimate looking links to other sites. However, these links that appear legitimate include a fragment identifier in the URL, so they look like the following, hxxps://ctyvs[.]link/login#. The hashtag at the end of the URL is a fragment identifier which references a specific part of the current web page. This means that the link will not redirect the user to other websites as it should, but instead remain on the same web page, though perhaps direct users back to the top of the current page. This is showcased in the screenshot below where you can see the link for Ways to Contact Us in the bottom left corner of the screen as hxxps://ctyvs[.]link/login#
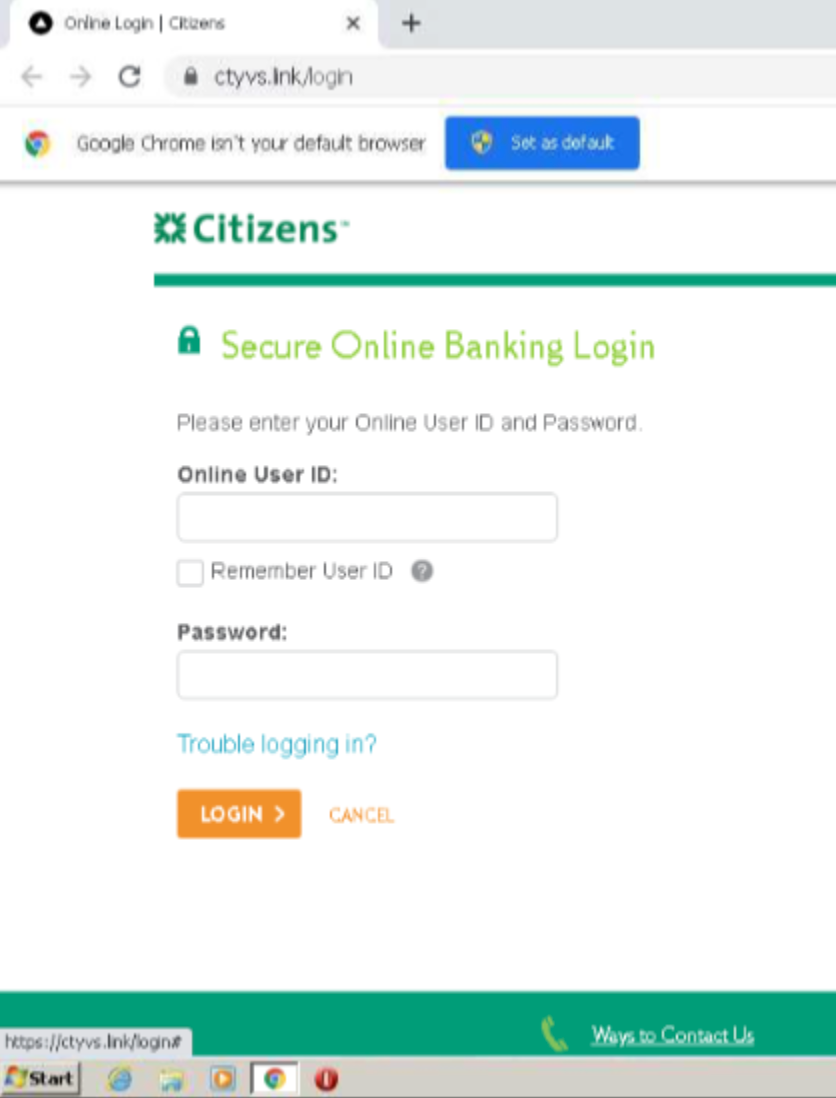
Why is this a threat ?
If successful, this attack would provide threat actors with access to sensitive personal information about the individual or corporate user, allowing threat actors to take control of their bank account and steal their money. Corporations using Citizens Bank would also be at risk of their internal network being compromised, if their credentials used at Citizens Bank correspond to those they use for work.
Domain brand impersonation does not just lead to theft of sensitive personal information, but could also result in malware infection for both private consumers and global corporations depending on the target and end goal of the threat actor. This occurs when stolen credentials are sold on the dark web, giving other threat actors the ability to conduct further attacks against the user(s) such as ransomware attacks. Such attacks could pose serious consequences for the company, including high monetary costs, disrupting business operations, exposure of confidential data and reputational damage.
-
A cyber incident of Citizens Bank could ultimately result in the loss of around 32 million USD.
-
Companies connected to Citizens Bank could run the risk of a data breach which as of 2022 could result in the loss of around 4,35 million USD.
-
If individual consumers were to become a victim of this attempt to gain their personal information over the internet, they could lose between 2-3 thousand USD.
Recommendations
-
If in doubt whether an email is legitimate, never click on any links. Go to the legitimate website’s domain instead via a search engine.
-
Always double check the domain name to make sure it is the legitimate one.
-
Never use the same credentials for work and personal accounts.
-
Use different passwords for online banking and shopping sites, for example, so if one of your accounts becomes compromised your other accounts will remain safe.
-
Incorporate Multi Factor Authentication where possible to keep your accounts safe even if the credentials are compromised.
Identification and threat analysis
Technical Report
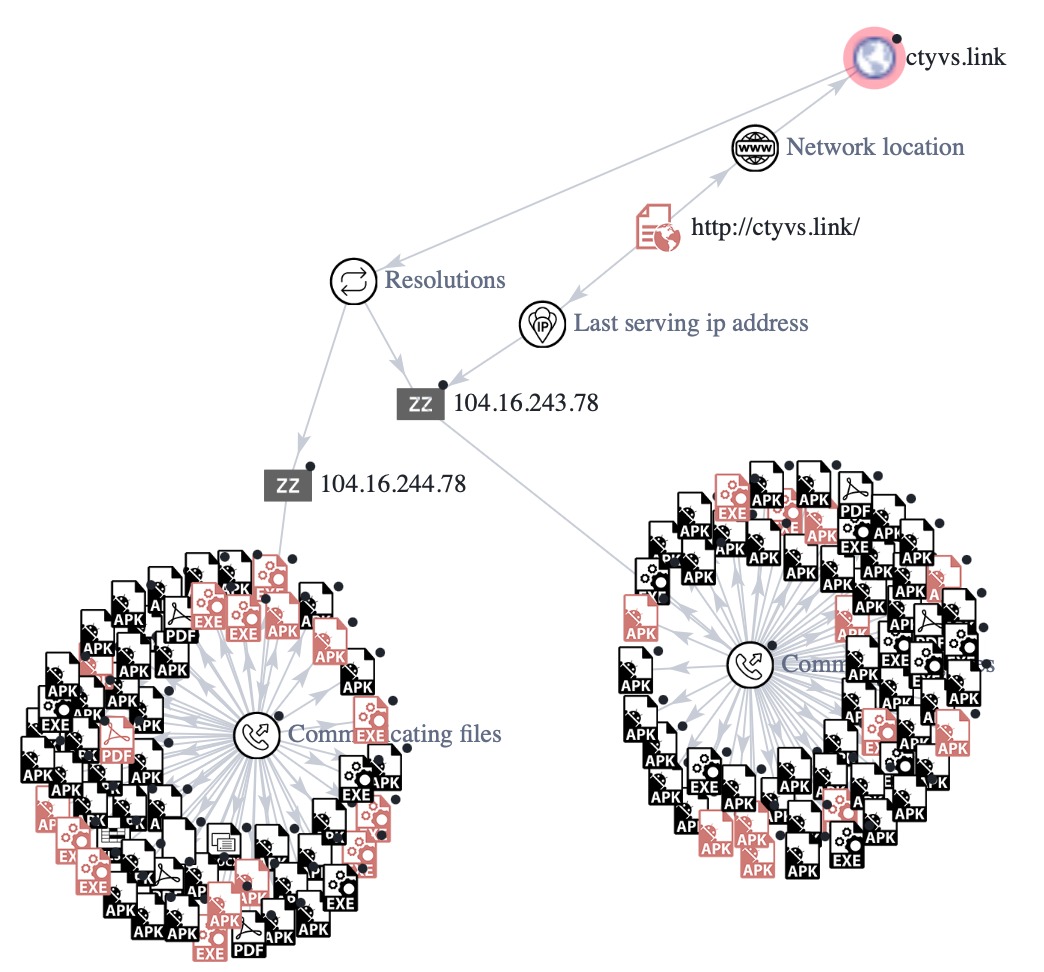
The technical report below helps emphasize the differences in terms of DNS records between the malicious domain, and the legitimate domain.
|
Domain |
ctyvs[.]link |
citizensbankonline[.]com |
|---|---|---|
|
Registrar |
Hostinger, UAB |
MarkMonitor, Inc.
|
|
Registrant Organisation |
Privacy Protect, LLC |
Citizens Financial Group Inc |
|
Registrant Country |
United States |
United States |
|
Domain Age |
1 days old Created 12 December 2022 |
8,895 days old Created on 6 August 1998
|
|
Certificate |
Issued by: Cloudflare, Inc. Issued to: Cloudflare, Inc. 11-12-2022 -> 11-12-2023 Valid for 1 year
|
Issued by: Entrust, Inc. Issued to: Citizens Financial Group Inc 13-04-2022 -> 13-04-2023 Valid for 1 year
|
|
Name Servers |
NS1.DIGITALOCEAN.COM |
A1-203.AKAM.NET
|
|
MX record |
N/A |
citizensbankonline-com.mail.protection.outlook.com
|
|
Last seen active |
13 December |
13 December |
|
IP address |
104.16.243.78, 104.16.244.78 Toronto, Ontario, Canada AS13335 Cloudflare, Inc. ISP: Cloudflare, Inc. Organisation: Cloudflare, Inc. |
23.216.81.249 Seattle, Washington, United States AS16625 Akamai Technologies, Inc. ISP: Akamai International, Inc. Organisation: Akamai International, BV
23.37.53.95 Frankfurt, Germany AS16625 Akamai Technologies, Inc. ISP: Akamai International, Inc. Organisation: Akamai International, BV |

How Bfore.Ai is protecting our customers
At Bfore.Ai, we work daily to ensure these phishing attacks get stopped before even reaching their targets. We are here to make your internet journey safer than it has ever been.
With more than 30K new malicious indicators per day we got you covered no matter where the attack comes from. Only 0.05% false positive rate, stop wasting time in false alerts chasing. By launching our PreCrime and PreEmpt technologies, we measure our anticipation from an attack starting, faster than attackers.
Accepting that the only defense is good detection, is accepting to be forever a victim. We believe in prevention more than response. Visit our website for more information !
Appendix
This document and its contents do not constitute, and are not a substitute for, legal advice. The outcome of a Security Risk Assessment should be utilized to ensure that diligent measures are taken to lower the risk of potential weaknesses be exploited to compromise data.
Although the Services and this report may provide data that Client can use in its compliance efforts, Client (not Bfore.Ai) is ultimately responsible for assessing and meeting Client’s own compliance responsibilities. This report does not constitute a guarantee or assurance of Client’s compliance with any law, regulation or standard.



.png)