AT&T Inc. is an American multinational telecommunications holding company. It is the world’s largest telecommunications company by revenue and the third largest provider of mobile telephone services in the U.S.
During our PreCrime internet scout of November 16th 2022 we identified suspicious markers across multiple vectors. One of those was this website spoof that could be targeting unsuspecting customers of AT&T.
The Attack
|
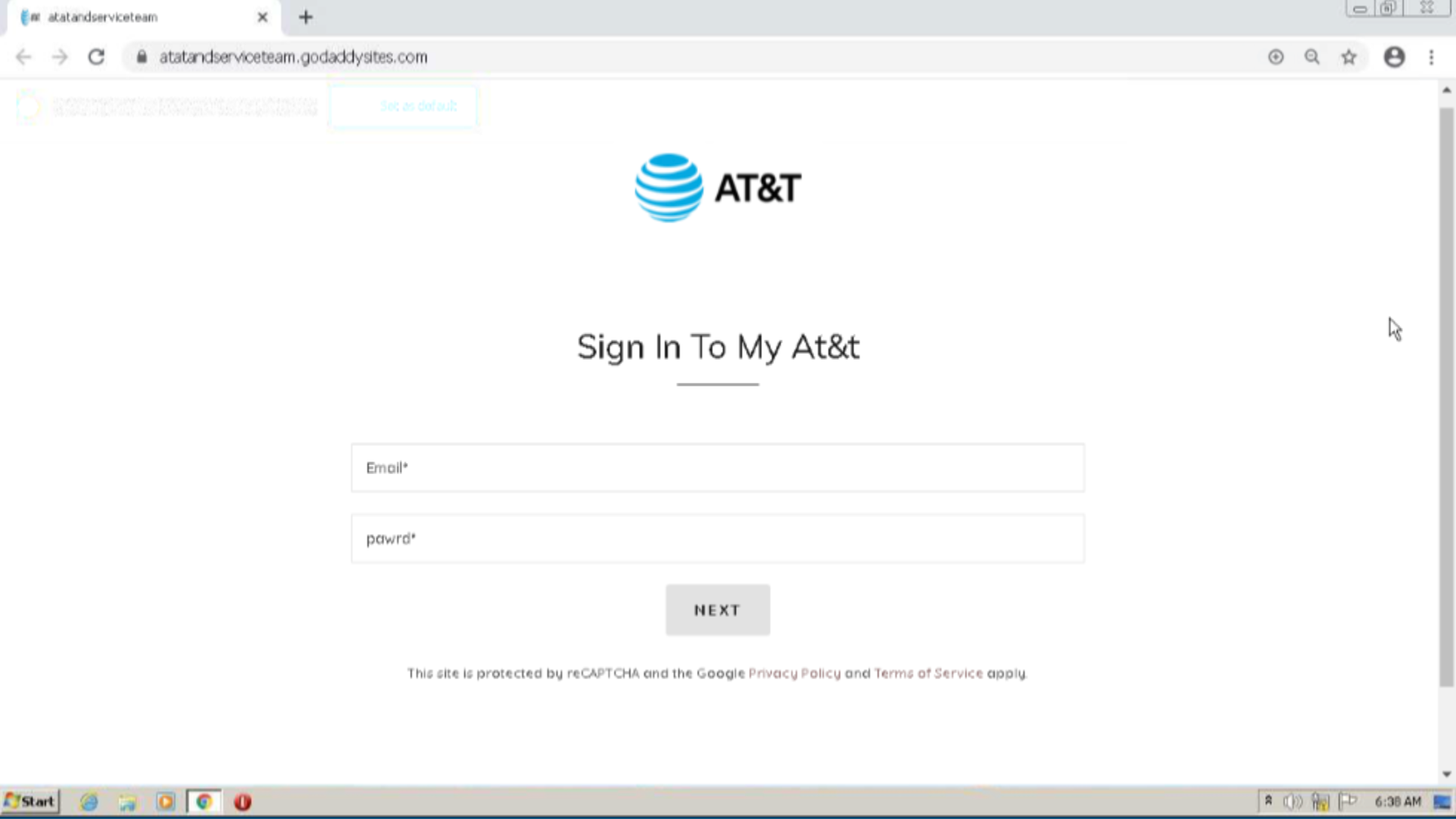
Malicious domain atatandserviceteam.godaddysites[.]com Created on November 15, 2022 |
Legitimate site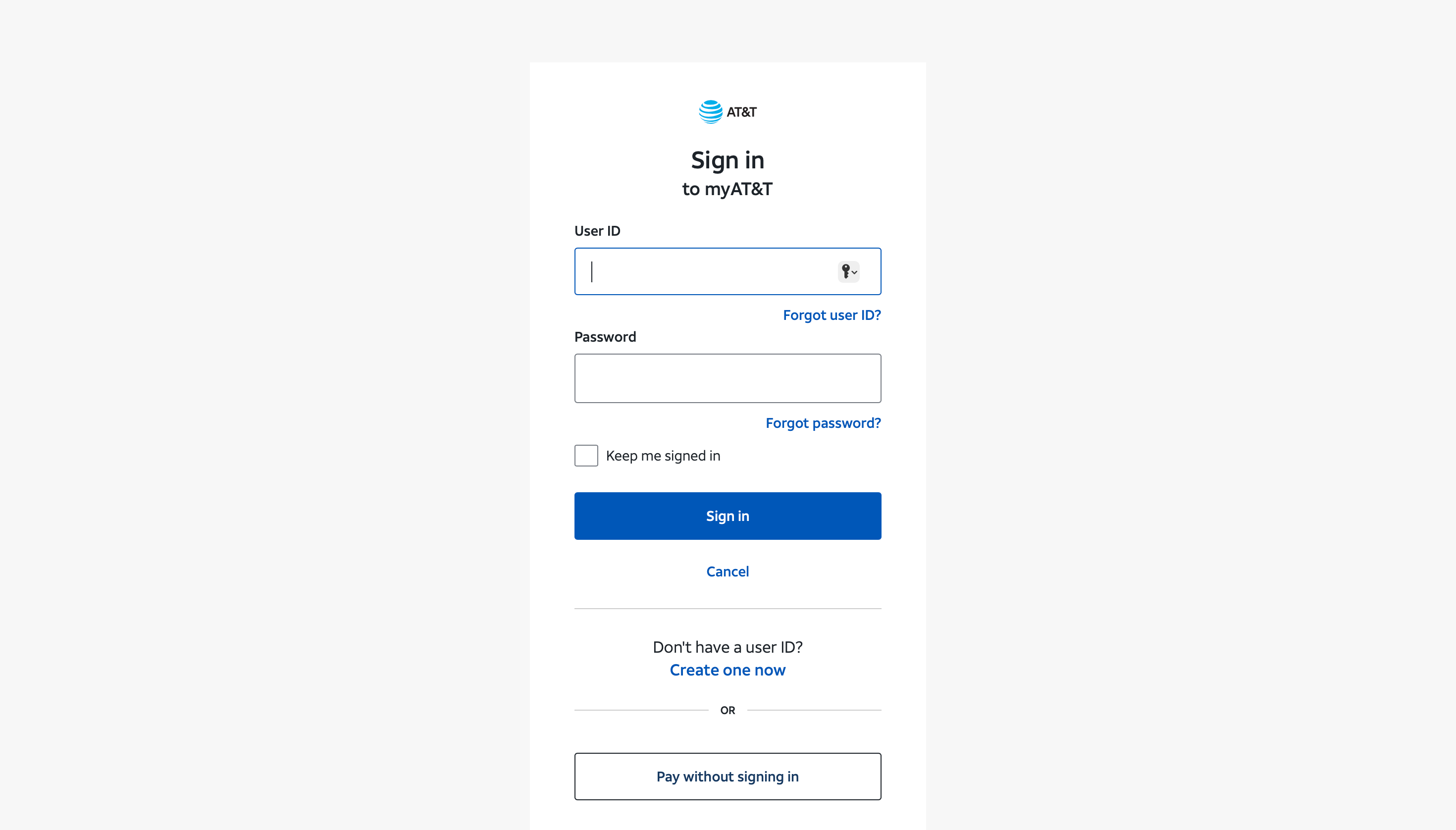
signin.att[.]com |
Why is this a threat ?
This malicious domain is an example of brand impersonation, where a threat actor impersonates a legitimate brand in order to steal sensitive information such as credentials and bank account numbers. In general, brands such as Apple, Netflix and DHL are popular targets for brand impersonation due to their trusted name as well as large and global customer base. Threat actors use various techniques in order to trick victims into believing the fake website is real. One such technique is typo squatting, wherein threat actors register a domain name that is similar to another organisation or brands own domain name. In many cases this includes exchanging a letter in the URL to something else, or adding another letter in the hopes that victims will not notice. An example of this could be, Appple[.]com, instead of Apple.com. Brand impersonation does not just lead to stolen credentials, but could also lead to theft of credentials, personal data and financial details, and/or result in malware infection for both private consumers and global corporations depending on the target and end goal of the threat actor.
In this instance, threat actors are targeting AT&T an American telecommunications company that provides network and communications solutions on a global scale with over 100 million subscribers and with more than 3.5 million businesses who employ AT&T services. With such a large and global customer base, threat actors are more likely to conduct a wide scale attack, targeting many people and companies at the same time in hopes that someone will fall for the scam.
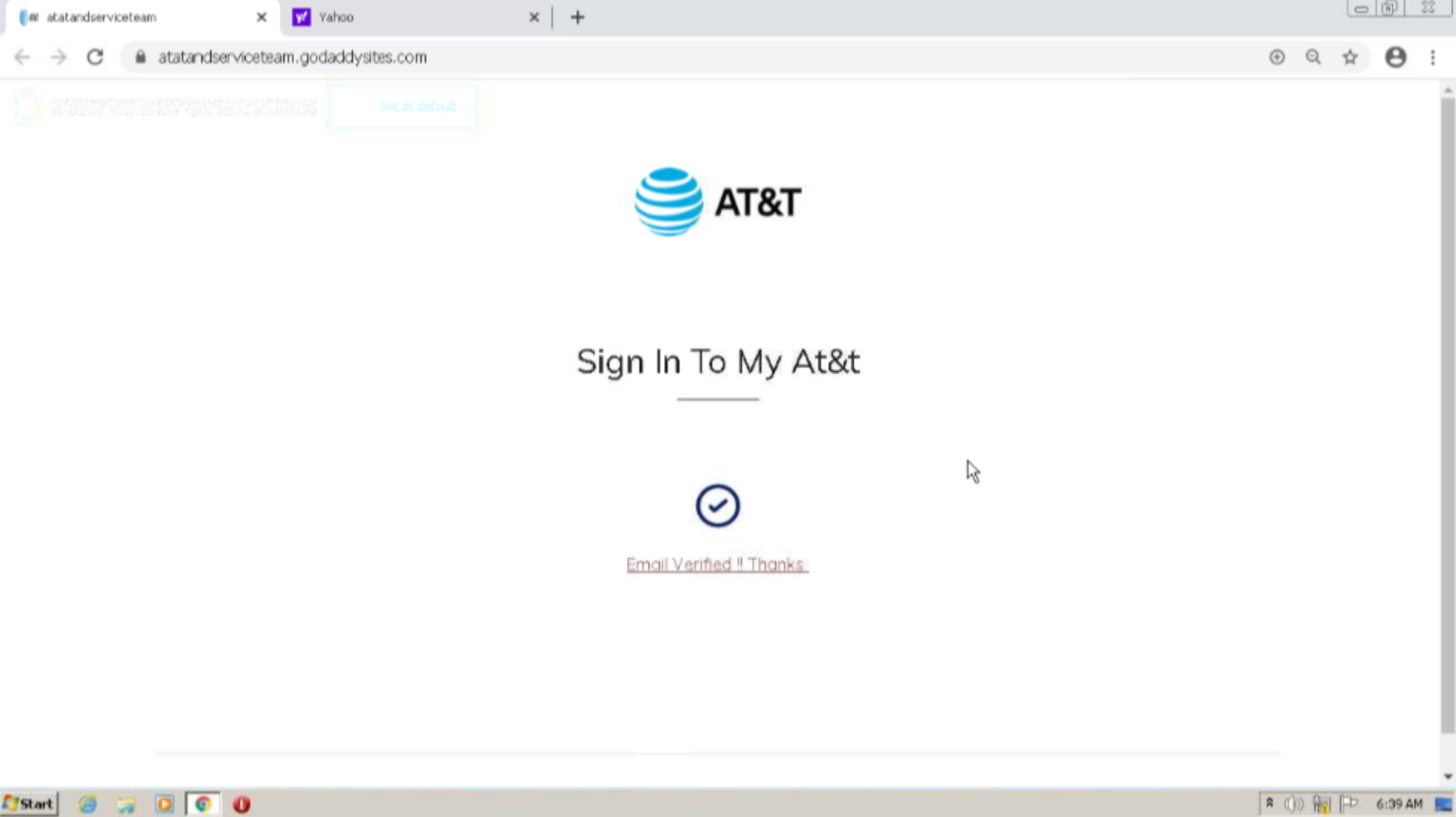
The malicious domain (atatandserviceteam.godaddysites[.]com) leads users to a scam AT&T login website where customers are asked to sign into their account. After entering fake credentials the below site appears, telling the user that the email had now been verified, Email Verified !! Thanks. This indicates that victims have most likely been sent an email with the malicious domain, asking them to verify their AT&T account due to some issue. Entering credentials into this sight will lead to the threat actor gaining access to the customers private details.
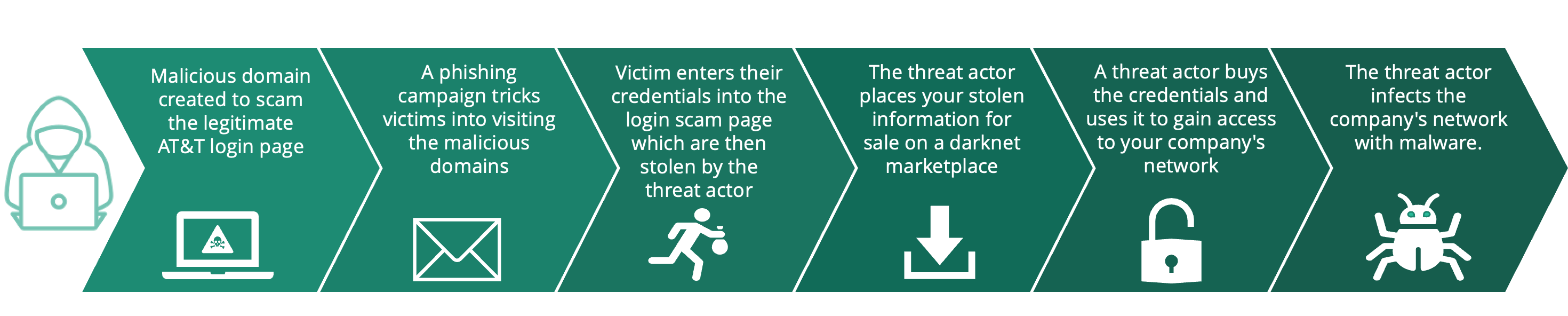
Once the credentials are stolen, they will likely be put for sale on dark web marketplaces, giving other threat actors access to the users private data. Some of these stolen credentials are likely to be work credentials, which would give threat actors access to a company’s internal network, leaving them vulnerable to financial loss, sensitive and confidential data leaking, as well as further cyber attacks such as ransomware. The attack path is illustrated below, detailing how a brand impersonation domain can lead to further attacks.
Threats to different groups:
-
With a yearly revenue of $163 Billion USD, a data breach of AT&T could result in the loss of up to 652 million USD!
-
Companies connected to AT&T could run the risk of a data breach resulting in a loss of around 4,35 million USD.
-
If individual consumer were to fall for this scam, they could lose between 2-3 thousand USD.
Technical Breakdown
Threat Indicators
-
Newly registered site – October 15 2022
-
Malicious domain impersonating AT&T asking users to validate their login credentials
-
Fake login credentials were verified by the malicious site
-
IP address connected to domain engages in malicious behavior
-
DNS records of malicious domain completely different to AT&T
Detection and Threat Analysis
Every site on the internet is found using an IP address, which is ‘translated’ from the domain name that is typed in. In the graph below, we can see that the malicious domain resolves to an IP (Internet Protocol) address with over 500 communicating files, many of them malicious (not all pictured). This IP address also resolves to around 200 other domains, many of which have also been marked as malicious. Since this domain has previously hosted malware and been connected to domains with malicious activity, the IP address has a low reputation that will most likely pose a risk to internet users who come across it by engaging in malicious behavior.
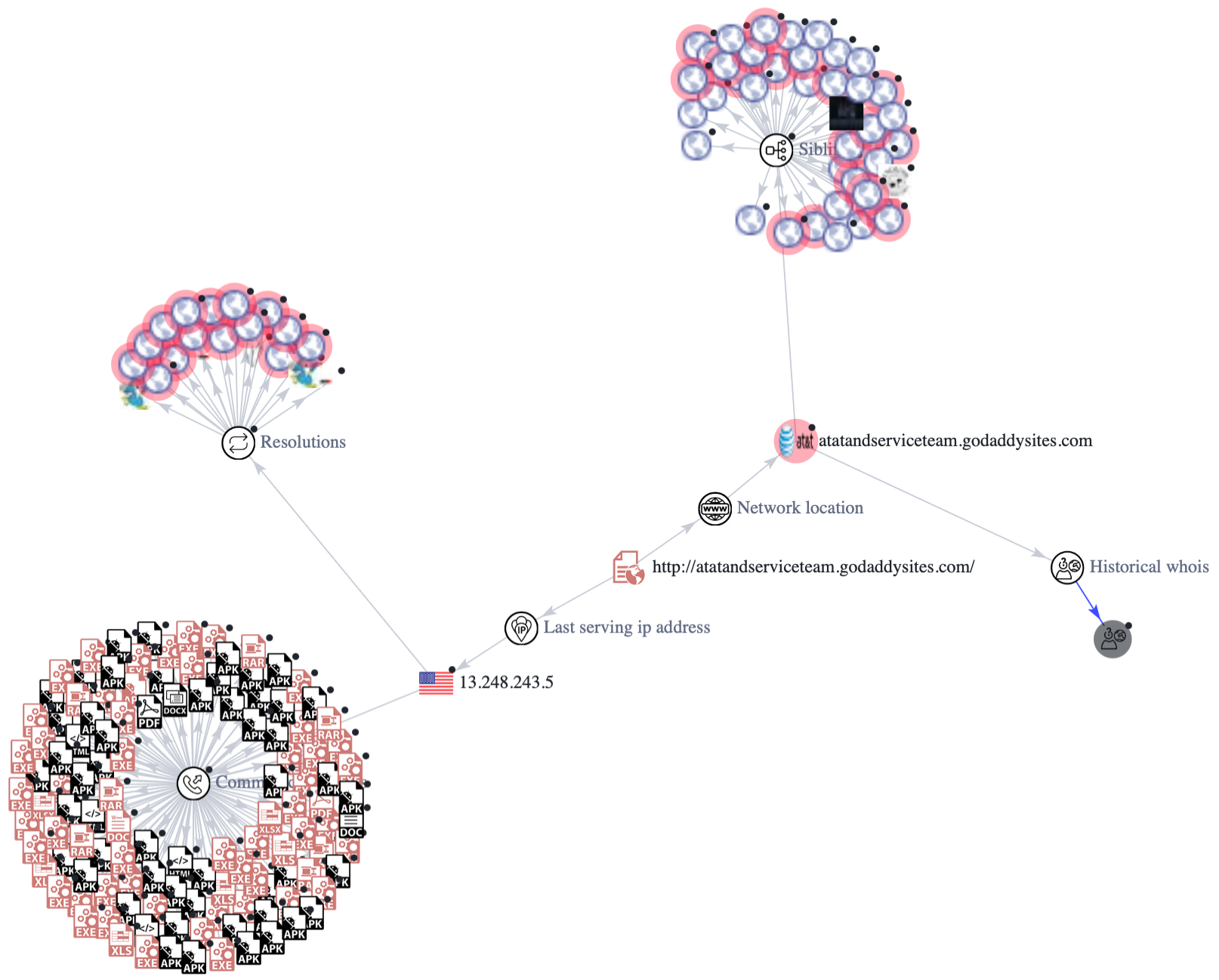 VirusTotal Graph
VirusTotal Graph
The Technical report below help emphasise the difference between the malicious domain, and the legitimate domain from AT&T. Below we can see that the DNS records are completely different to the DNS records of the legitimate website. The main point of interest is that the legitimate domain is registered under the company name, AT&T SERVICES, INC., whereas the malicious domain one does not provide details of this. Legitimate domains will always publicly demonstrate the registrar organisation for validity. See further details below.
Technical Report
|
Domain |
atatandserviceteam.godaddysites[.]com |
signin.att[.]com |
|---|---|---|
|
Registrar |
GoDaddy.com, LLC |
CSC Corporate Domains, Inc. |
|
Registrant Organisation |
Domains By Proxy, LLC |
AT&T SERVICES, INC. |
|
Registrant Country |
United States |
United States |
|
Domain Creation and Expiration |
1 day old Created on 2022-11-15 |
13,353 days old Created on 1986-04-25 |
|
Certificate |
Issued by: GoDaddy.com, Inc. Issued to: *.godaddysites.com Domain validated 19-05-2022 -> 20-06-2023 Valid for over 1 year |
Issued by: DigiCert Inc Issued to: AT and T Services, Inc. Organization validated 30-06-2022 -> 30-06-2023 Valid for 1 year |
|
Name Servers |
cns1.secureserver.net cns2.secureserver.net |
ns0133.secondary.cloudflare.com ns0109.secondary.cloudflare.com |
|
MX record |
N/A |
None for the domain
For att.com: mx0a-00191d01.pphosted.com mx0b-00191d01.pphosted.com |
|
Last seen active |
16 November 2022 |
16 November 2022 |
|
IP address |
13.248.243.5, 76.223.105.230 Washington, United States AS16509 Amazon.com, Inc. ISP: Amazon.com, Inc. |
144.160.36.42, 144.160.155.43 Indiana, United States AS797 AT&T Services, Inc. ISP: AT&T Services, Inc. |
How Bfore.Ai is protecting our customers
At Bfore.Ai, we work daily to ensure these phishing attacks get stopped before even reaching their targets. We are here to make your internet journey safer than it has ever been.
With more than 30K new malicious indicators per day we got you covered no matter where the attack comes from. Only 0.05% false positive rate, stop wasting time in false alerts chasing. By launching our PreCrime and PreEmpt technologies, we measure our anticipation from an attack starting, faster than attackers.
Accepting that the only defense is good detection, is accepting to be forever a victim. We believe in prevention more than response. Visit our website for more information !
Bfore.Ai’s recommendations
Every day, adversarial tactics become more collaborative, technologically advanced, and rapid – and at this rate, you simply can’t afford to wait for the next attack before you react. Here are some recommendations from our team :
- Pay close attention to the URL
- Check connection security indicators (the lock)
- Read emails carefully
- Look for trust seals
Appendix
This document and its contents do not constitute, and are not a substitute for, legal advice. The outcome of a Security Risk Assessment should be utilized to ensure that diligent measures are taken to lower the risk of potential weaknesses be exploited to compromise data.
Although the Services and this report may provide data that Client can use in its compliance efforts, Client (not Bfore.Ai) is ultimately responsible for assessing and meeting Client’s own compliance responsibilities. This report does not constitute a guarantee or assurance of Client’s compliance with any law, regulation or standard.