.png)
Banco Patagonia is an Argentinian bank founded in 1976 and part of the Merval, the main stock index of the Buenos Aires stock exchange.
During our PreCrime internet scout of November 4th 2022 we identified suspicious markers across multiple vectors. One of those was this website spoof that could be targeting unsuspecting customers of Banco Patagonia.
The Attack
Target:
- Customers of Banco Patagonia
Possible threats:
- Credential harvesting and financial gain – After luring users to the site, they are asked to login to their Banco Patagonia account using their credentials, allowing threat actors to take control of their bank account and steal their money. Customers may be led to the website via a phishing campaign, asking them to click on a link to resolve an issue with their account for example.
- Since Banco Patagonia provides services for both individuals as well as small and medium sized companies, companies connected to Banco Patagonia are also at risk of stolen credentials. With 51% of people using the same passwords for both their work and personal accounts, any stolen credentials may provide threat actors with internal access to a company network leaving them vulnerable to financial loss, sensitive and confidential data leaking, as well as further cyber attacks such as ransomware.
Such a scam could result in a loss of around 2.3-3.5 millions dollar loss for the bank.
|
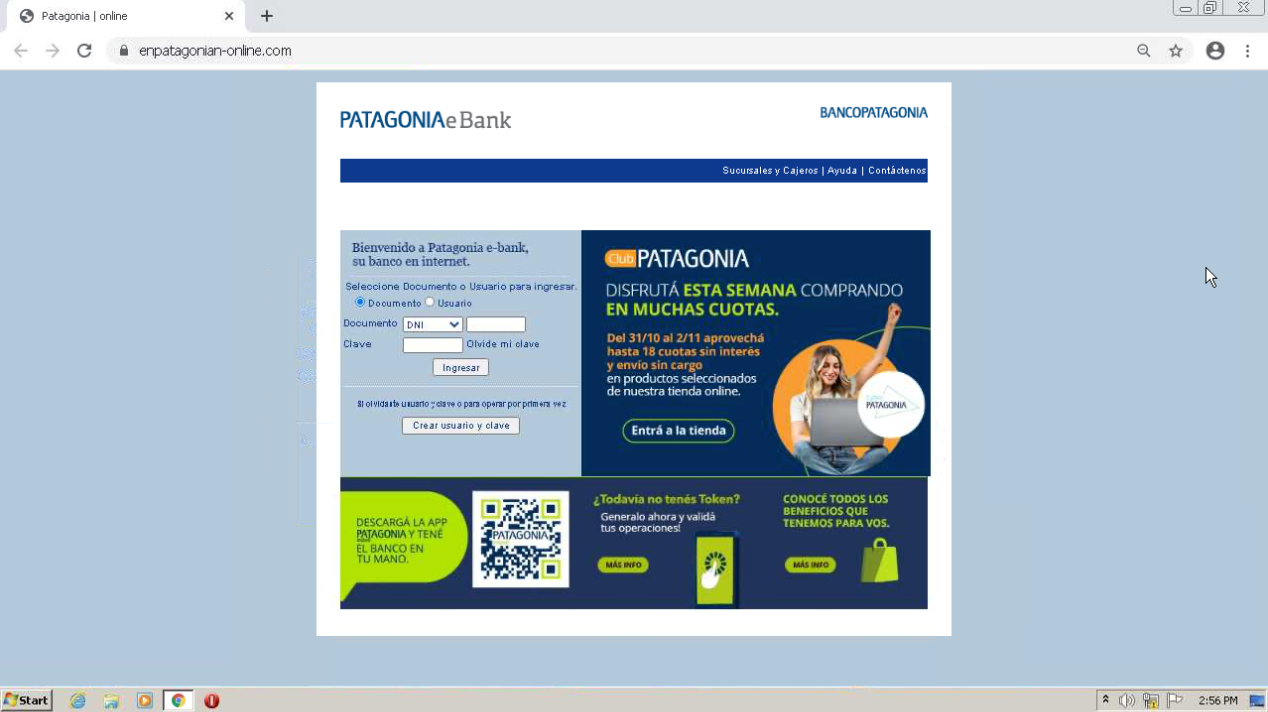
Malicious sites: enpatagonian-online[.]com |
Legitimate site: bancopatagonia[.]com[.]ar
|
|
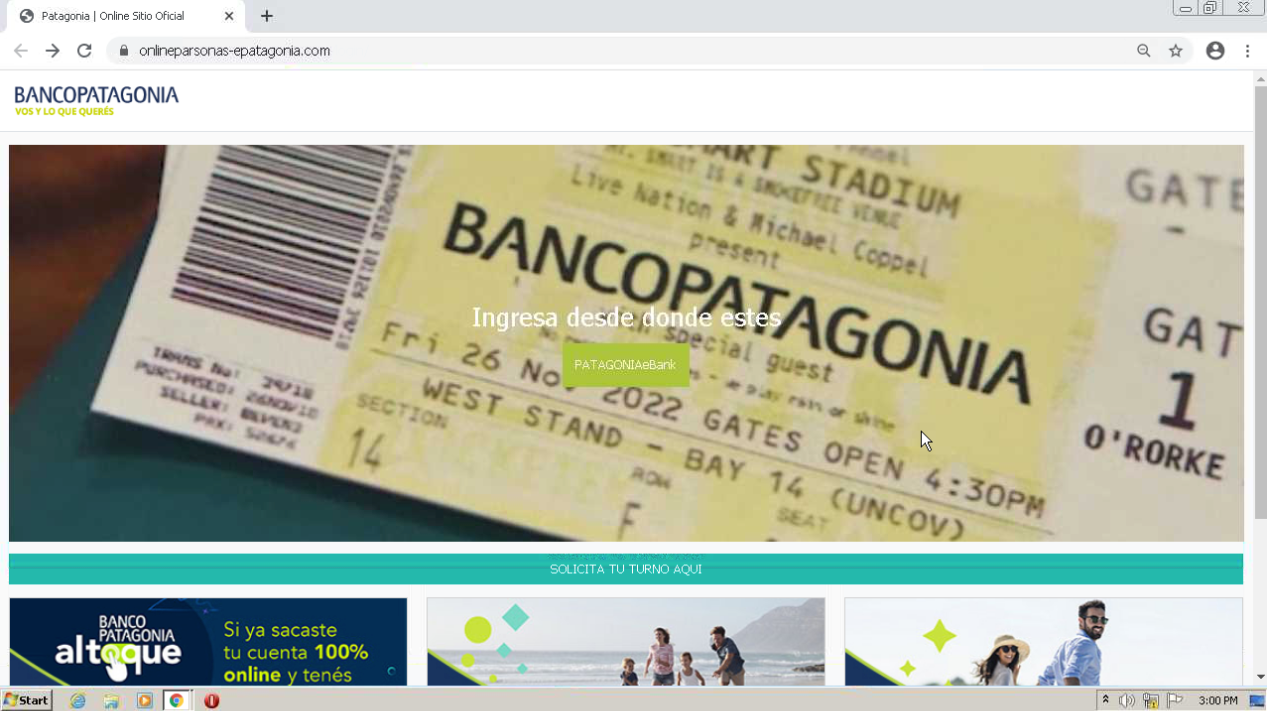
onlineparsonas-epatagonia[.]com and multipatagonionline-inicio[.]com
|
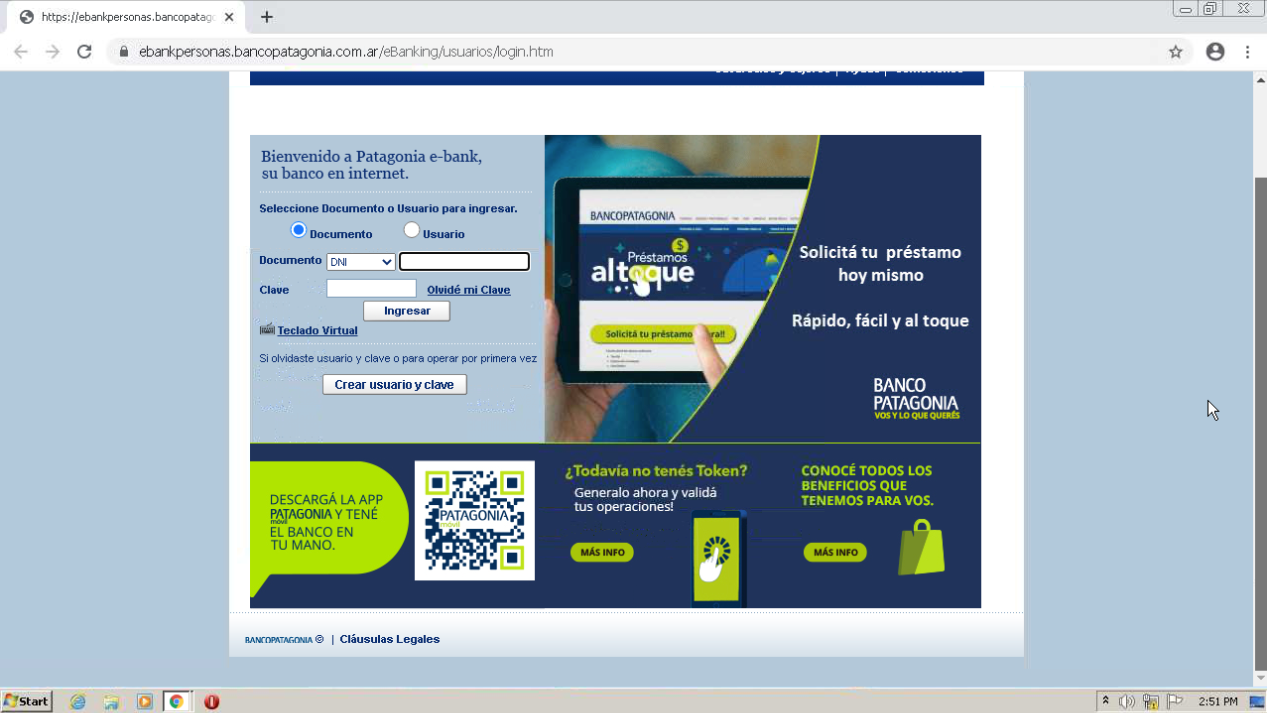
Legitimate bank login page: ebankpersonas[.]bancopatagonia[.]com[.]ar/eBanking/usuarios/login[.]htm
|
|
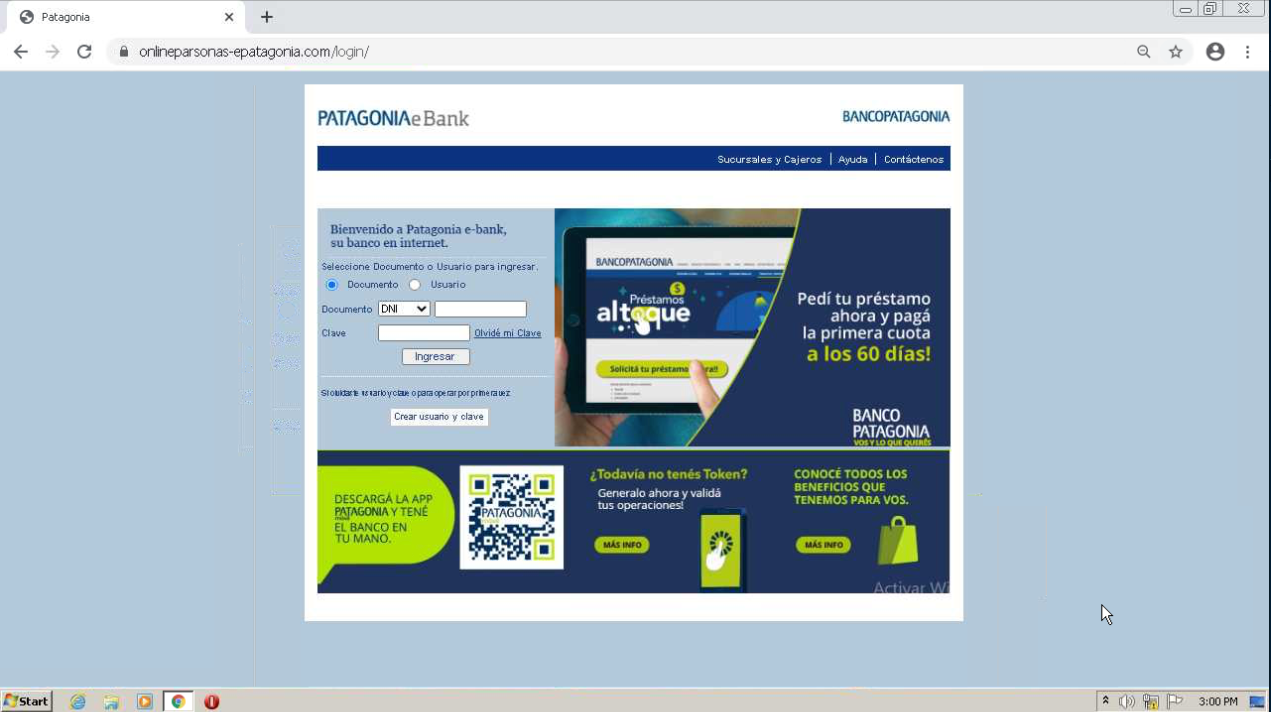
Leads to: onlineparsonas-epatagonia[.]com/login multipatagonionline-inicio[.]com/login
|
Technical Breakdown
Threat Indicators
- Malicious domains impersonating Banco Patagonia
- DNS records of malicious domain different to Banco Patagonia
- Newly registered sites – November 1-3 2022
- MX record indicates domain may be part of a phishing campaign
- SSL certificates expire after three months
- IP address blacklisted
Detection and Threat Analysis
The malicious domains are targeting Banco Patagonia, an Argentinian commercial bank owned by Banco de Brasil and headquartered in Buenos Aires. The provides a range of financial solutions for individuals, corporations, small and medium sized companies, private banking, and institutional customers. The malicious domains were created between November 1-3, 2022 and identified by Bfore.Ai November 4, 2022.
-
Two of the malicious sites (onlineparsonas-epatagonia[.]com and multipatagonionline-inicio[.]com) first show users a ‘home page’ for the bank. All links on these sites simply refresh the website, except for the link in the middle of the website, which leads users to a login page that mirrors the legitimate one from Banco Patagonia. The final malicious site (enpatagonian-online) leads users directly to a cloned login page. On the malicious login pages, all links on the website simply refresh the page, ensuring that victims stay on the same login page and are therefore, more likely to simply enter their bank credentials.
-
The DNS records are different to the DNS records of the legitimate website. The main point of interest is that the legitimate domain is registered under it’s own organisations name (Banco Patagonia S.A), whereas the malicious domains are all registered under different registrars, with different certificates, and IP addresses without including an organisation name. Legitimate companies will always include their organisation name in DNS records in order to verify their legitimacy as Banco Patagonia has done. See further details and comparison between the malicious and legitimate domain below.
-
While the domains all show different DNS records, their almost identical website structure and registration dates indicate that it is most likely the same threat actor behind all three domains.
-
One of the domains (multipatagonionline-inicio) has registered MX records, giving the threat actors the ability to accept and send email messages on behalf of the domain names. It indicates that the threat actors may be setting up the domain to be part of a phishing campaign that leads to the malicious domain.
-
The registered SSL certificates expire after three months indicating malicious intent. Legitimate companies will more commonly ensure their certificate lasts at least 1 year and as mentioned earlier, include their organisation name (Banco Patagonia S.A).
-
The domains resolve to different IP addresses in different locations (Singapore, Brazil and the United States) where two of them have been blacklisted by spfbl.
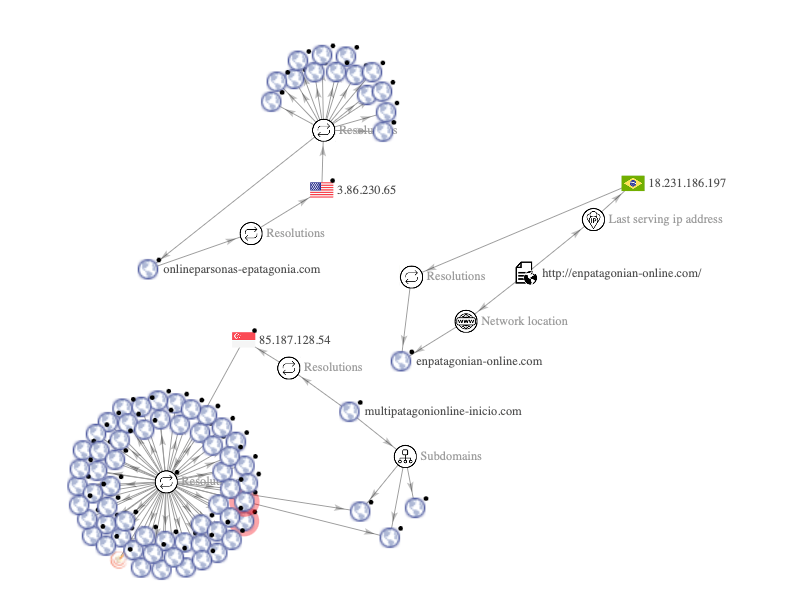 VirusTotal Graph
VirusTotal Graph
DNS Record
| Domain | enpatagonian-online[.]com | onlineparsonas-epatagonia[.]com | multipatagonionline-inicio[.]com | bancopatagonia[.]com[.]ar |
|---|---|---|---|---|
| Domain Creation and Expiration | Created on 2022-11-03 Expires on 2023-11-03 Updated on 2022-11-03 1 day old |
Created on 2022-11-03 Expires on 2023-11-03 Updated on 2022-11-03 1 day old |
Created on 2022-11-01 Expires on 2023-11-01 Updated on 2022-11-01 3 day old |
Created on 1999-12-25 Expires on 2022-12-25 Updated on 2021-12-20 8250 days old |
| Registrant | DreamHost, LLC | Gandi SAS | Gandi SAS | Nicar |
| Registrar country | United States | Netherlands | Netherlands | Argentina |
| Certificate | Issued by: Let’s Encrypt
Issued to: The domain 03-11-2022 -> 01-02-2023 Valid for 3 months |
Issued by: ZeroSSL
Issued to: The domain 02-11-2022 -> 01-02-2023 Valid for 3 months |
Issued by: cPanel, Inc.
Issued to: The domain 31-10-2022 -> 30-01-2023 Valid for 3 months |
Issued by: DigiCert Inc
Issued to: Banco Patagonia S.A 10-01-2022 -> 11-02-2023 Valid for over 1 year |
| Name Servers | ns1.dreamhost.com
ns2.dreamhost.com ns3.dreamhost.com |
ns1.dns-parking.com
ns2.dns-parking.com |
ns1.a2hosting.com
ns2.a2hosting.com ns3.a2hosting.com ns4.a2hosting.com |
ns1.bancopatagonia.com.ar
ns2.bancopatagonia.com.ar |
| MX record | N/A | N/A | mail.multipatagonionline-inicio.com | mailgw1.bancopatagonia.com.ar
mailgw2.bancopatagonia.com.ar |
| Last seen active | 4 November 2022 | 4 November 2022 | 4 November 2022 | 4 November 2022 |
| IP address | 18.231.186.197
São Paulo, Brazil AS16509 Amazon.com, Inc. ISP: Amazon Technologies Inc. |
3.86.230.65
Virginia, United States AS16509 Amazon.com, Inc. ISP: Amazon Technologies Inc. |
85.187.128.54
Singapore, Singapore AS55293 A2 Hosting, Inc. ISP: A2 Hosting, Inc |
45.224.184.137
Buenos Aires, Argentina AS265859 BANCO PATAGONIA S.A ISP: BANCO PATAGONIA S.A |
| Blacklisted | dnsbl.spfbl.net | dnsbl.spfbl.net | N/A | N/A |
How Bfore.Ai is protecting our customers
At Bfore.Ai, we work daily to ensure these phishing attacks get stopped before even reaching their targets. We are here to make your internet journey safer than it has ever been.
With more than 30K new malicious indicators per day we got you covered no matter where the attack comes from. Only 0.05% false positive rate, stop wasting time in false alerts chasing. By launching our PreCrime and PreEmpt technologies, we measure our anticipation from an attack starting, faster than attackers.
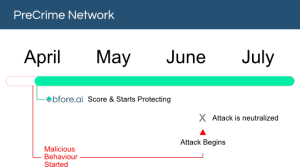
Accepting that the only defense is good detection, is accepting to be forever a victim. We believe in prevention more than response. Visit our website for more information !
Bfore.Ai’s recommendations
Every day, adversarial tactics become more collaborative, technologically advanced, and rapid – and at this rate, you simply can’t afford to wait for the next attack before you react. Here are some recommendations from our team :
- Pay close attention to the URL
- Check connection security indicators (the lock)
- Read emails carefully
- Look for trust seals
Appendix
This document and its contents do not constitute, and are not a substitute for, legal advice. The outcome of a Security Risk Assessment should be utilized to ensure that diligent measures are taken to lower the risk of potential weaknesses be exploited to compromise data.
Although the Services and this report may provide data that Client can use in its compliance efforts, Client (not Bfore.Ai) is ultimately responsible for assessing and meeting Client’s own compliance responsibilities. This report does not constitute a guarantee or assurance of Client’s compliance with any law, regulation or standard.