
Garmin Express is an application designed to manage Garmin devices. It is used for device registration, syncing Fitness data with Garmin Connect, map updates and software updates, and much more.
During our PreCrime internet scout of September 15th 2022 we identified suspicious markers across multiple vectors. One of those was this website spoof that could be targeting unsuspecting Garmin customers.
The Attack
Target:
Garmin customers, people who own/use a Garmin device.
Possible threats:
Arkei/Vidar Trojan Malware. An info stealer malware that steals documents, cookies and browser history (including from Tor) including banking and credit card details, currency from different cryptocurrency wallets, data from two-factor authentication software and text messages.
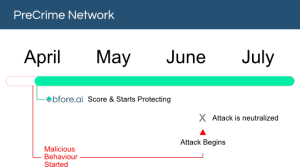
Timeline


These malicious domains allow users to download a malicious file (discussed further below).
Additionally, the domains, garminexprenss.site and garminexcpress.site are sites created to provide more information about Garmin Express. These sites will most likely be used to direct individuals to the malicious garmin domains shown above to seem more legitimate.


Technical Breakdown
Threat Indicators
- Malicious domains targeting and impersonating Garmin
- Executable files are dropped on all the malicious sites after they are loaded
- Trojan Malware downloaded
- Newly registered sites – September 14 2022
- All domains registered on the same IP address and name servers
- All domains have MX records
The domains garminexprenss.site, garminexcpress.site, garminexcpress.website and garminexprenss.us all work to impersonate Garmin, an American, Swiss-domiciled multinational technology company founded in 1989 that specializes in GPS technology. These sites are specifically targeting Garmin Express, an application designed to manage Garmin devices that can only be downloaded on a windows or Mac computer. These sites were created September 14, 2022 and detected by Bfore.ai September 15, 2022.
- All the domains are registered on the same IP address with the same name servers and MX records. The IP address has malicious traffic and is communicating with .EXE and .APK malicious files. Additionally, the MX records give the threat actors the ability to accept email messages on behalf of the domain names. Additionally, it indicates that the threat actors may be setting up these domains to be part of a phishing campaign that leads to the malicious domains.
- Executable files are dropped on all the malicious sites after they are loaded.
- The malicious domains impersonating the Garmin Express download site, lead to the download of a Trojan Malware.


Detection and Threat Analysis
These malicious sites are most likely set up to work together to create a scam crossing multiple domains to make the users more convinced of its validity.
1. Luring victims
The domains, garminexprenss.site and garminexcpress.site are sites created to provide more information about Garmin Express. These sites will most likely be used to direct individuals to the malicious garmin domains (garminexcpress.website and garminexprenss.us ) to seem more legitimate.
2. Downloading Trojan Malware ‘Garmin Express’
The malicious sites, garminexcpress.website, garminexprenss.us have replicated the original website. No other links on these malicious sites work except for the download buttons. This is a clear indicator that these sites are fake and duplicated and only created to make users click the download buttons. Once the download button is clicked a file starts downloading. The difference between the malicious and the legitimate download is clear:
- Malicious executable: Garmin-express.zip
Legit executable: GarminExpress.exe
- (The application can be downloaded via the legitimate website here: www.garmin.com/en-US/software/express/)


The ZIP file (garmin-express.zip) has been identified as a variant of the Arkei/Vidar Trojan Malware. This malware is an infostealer first introduced in November 2018, that steals documents, cookies and browser history (also from Tor) including banking and credit card details, currency from different cryptocurrency wallets (Litecoin, Bitcoin, Ethereum, Zcash, and DashCore), data from two-factor authentication software and text messages, and it can take screenshots. After collecting all targeted information, the malware archives the stolen information and sends it to a control server. As a final step, the malware will remove all traces of itself on the infected system.
The malware, first introduced in November 2018, is presumed originate in a Russian-speaking country since the execution of the malware is configured to stop if it detects that it is being run on a machine that has a Russian keyboard layout or is located in one of the former USSR nations.
WhoIs Record

IP address

MX Record

How Bfore.Ai is protecting our customers
At Bfore.Ai, we work daily to ensure these phishing attacks get stopped before even reaching their targets. We are here to make your internet journey safer than it has ever been.
With more than 30K new malicious indicators per day we got you covered no matter where the attack comes from. Only 0.05% false positive rate, stop wasting time in false alerts chasing. By launching our PreCrime and PreEmpt technologies, we measure our anticipation from an attack starting, faster than attackers.
Accepting that the only defense is good detection, is accepting to be forever a victim. We believe in prevention more than response. Visit our website for more information !
Bfore.Ai’s recommendations
Every day, adversarial tactics become more collaborative, technologically advanced, and rapid – and at this rate, you simply can’t afford to wait for the next attack before you react. Here are some recommendations from our team :
- Pay close attention to the URL
- Check connection security indicators (the lock)
- Read emails carefully
- Look for trust seals
Appendix
This document and its contents do not constitute, and are not a substitute for, legal advice. The outcome of a Security Risk Assessment should be utilized to ensure that diligent measures are taken to lower the risk of potential weaknesses be exploited to compromise data.
Although the Services and this report may provide data that Client can use in its compliance efforts, Client (not Bfore.Ai) is ultimately responsible for assessing and meeting Client’s own compliance responsibilities. This report does not constitute a guarantee or assurance of Client’s compliance with any law, regulation or standard.





