.jpeg)
We’ve previously discussed job recruitment scams, but in terms of employee scams, unfortunately it doesn’t just stop there. While you might be thinking, “yes! I’ve started a new job and it’s not a scam!“ (sorry for inflicting you with a constant stream of scepticism and paranoia), scams continue in the workplace and can represent a huge threat to your company.
Social engineering scams are unfortunately still one of the most exploited initial attack vectors to gain entry into a company’s internal network. Due to this, employees are often viewed as a potential weak point in an organisations cybersecurity defences and therefore often become the initial targets in attacks against your brand. And if a threat actor is snooping around your confidential and sensitive files it could put your brand at risk of financial and reputational damage.
As a company it’s incredibly important to strengthen your cyber resilience by understanding which threats you and your employees may be targeted by and ensuring adequate security awareness training.
So without further ado, let’s get into it.
Why are employees targeted?
Employee credentials, such as usernames and passwords, can provide threat actors with access to an enterprises internal systems and data. These credentials can either be used by the threat actor to conduct further attacks, or sold to other threat actors so they can exploit your company instead. What the threat actor chooses to do with the stolen data really depends on their motives and end goals.
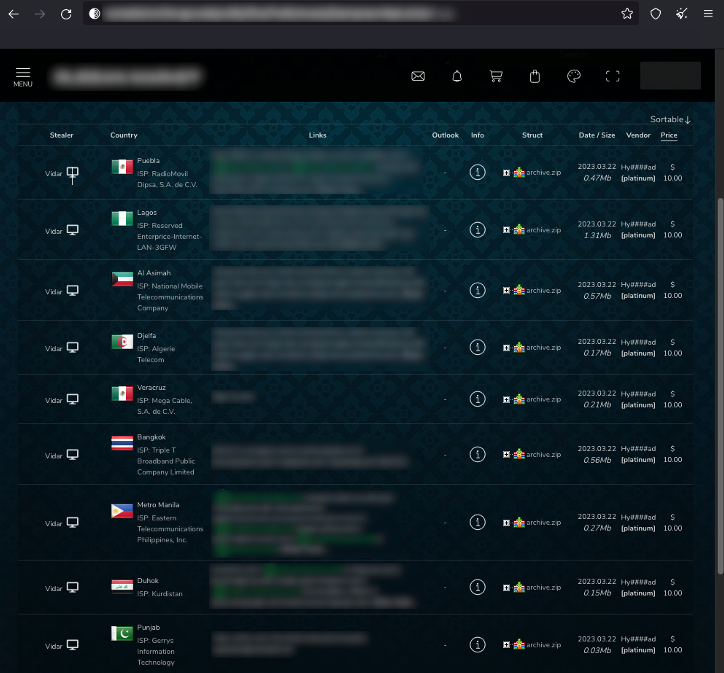 A Russian marketplace selling stolen account data from various websites
A Russian marketplace selling stolen account data from various websites
With the right credentials, a threat actor may be able to:
-
Access confidential information: Employee credentials can provide access to confidential information such as financial data, customer information, and intellectual property.
-
Financial theft: If a threat actor gains access to an employee’s banking information or can convince an employee to transfer funds, they can steal money from the company. Simple yet painful.
-
Install malware: Threat actors may use employee credentials to gain access to an organisations systems and install malware or ransomware that can be used to steal company and customer data and/or disrupt critical operations.
-
Privilege Escalation: By posing as a trusted colleague or manager, a threat actor may be able to convince a higher-level employee to divulge sensitive information that will grant them elevated permissions on the network.
So let’s take a look at the following equation:
Employees have direct access to sensitive information and systems
+
43% of companies don’t have organization wide security awareness training
=
Easy access into the company’s internal networks
Now that we have that in the clear, let’s move on.
How are employees targeted?
Employees will most likely be contacted through email (phishing), social media, phone calls (vishing) and text messages (smishing). Here the attacker will use various social engineering tactics including flattery, intimidation or urgency to manipulate them into divulging sensitive information, clicking on a link and/or opening an attachment. Here are some attack methods we’ve seen:
Malicious login site
Threat actors may attempt to lure your employee into clicking on a link that will send them to a brand impersonated website where they are asked to login to their Microsoft office account. Alternatively the attacker may ask them to login to their employee account due to an issue by referencing a file that they need to access, such as in the examples below.
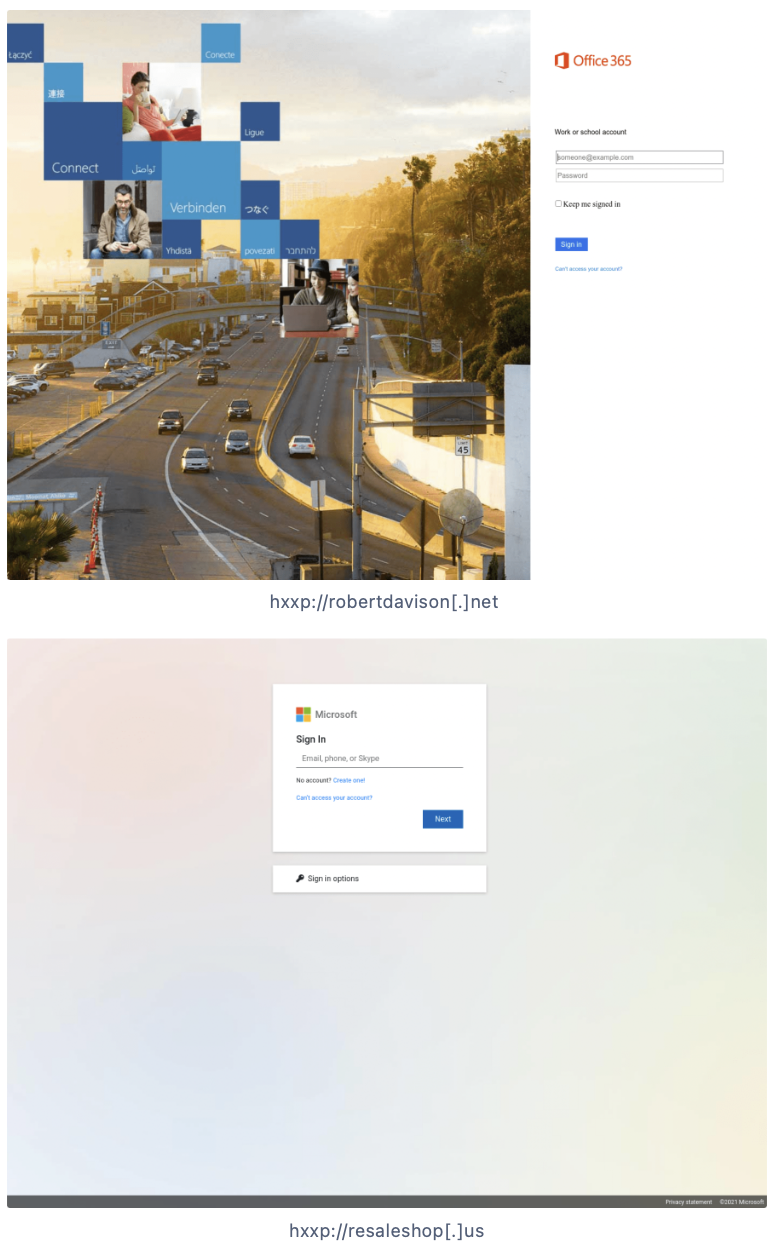
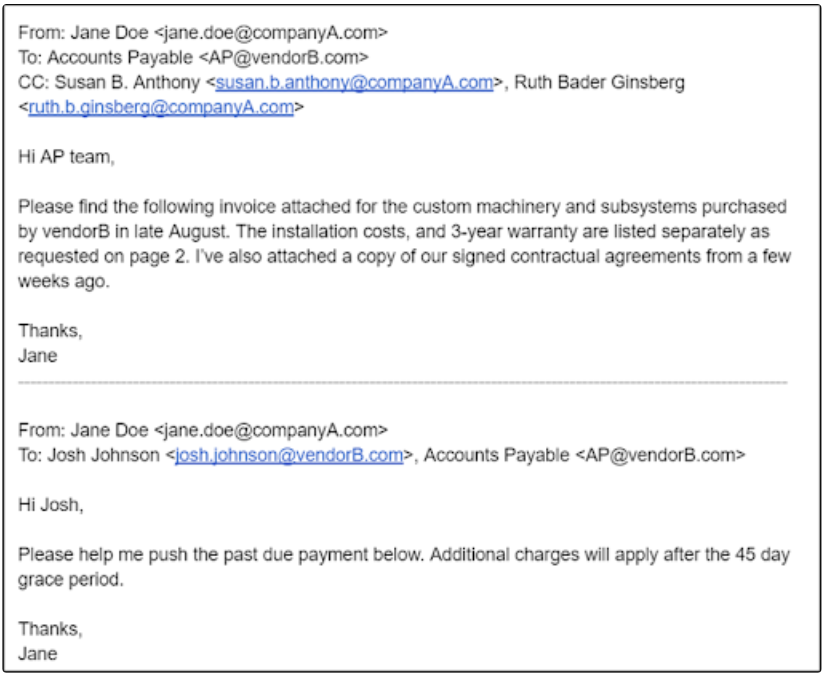
Third party vendor impersonation
In these attacks the threat actor will impersonate the target company’s third-party partner or provider in an email to employees asking them to take an action, such as transferring funds or goods.
The FBI more recently warned against a new scam that defrauds U.S. vendors by placing an order for a bulk purchase of commercial goods on behalf of companies. Among the goods targeted in this type of fraud are construction materials, agricultural supplies, IT equipment, and solar energy products.
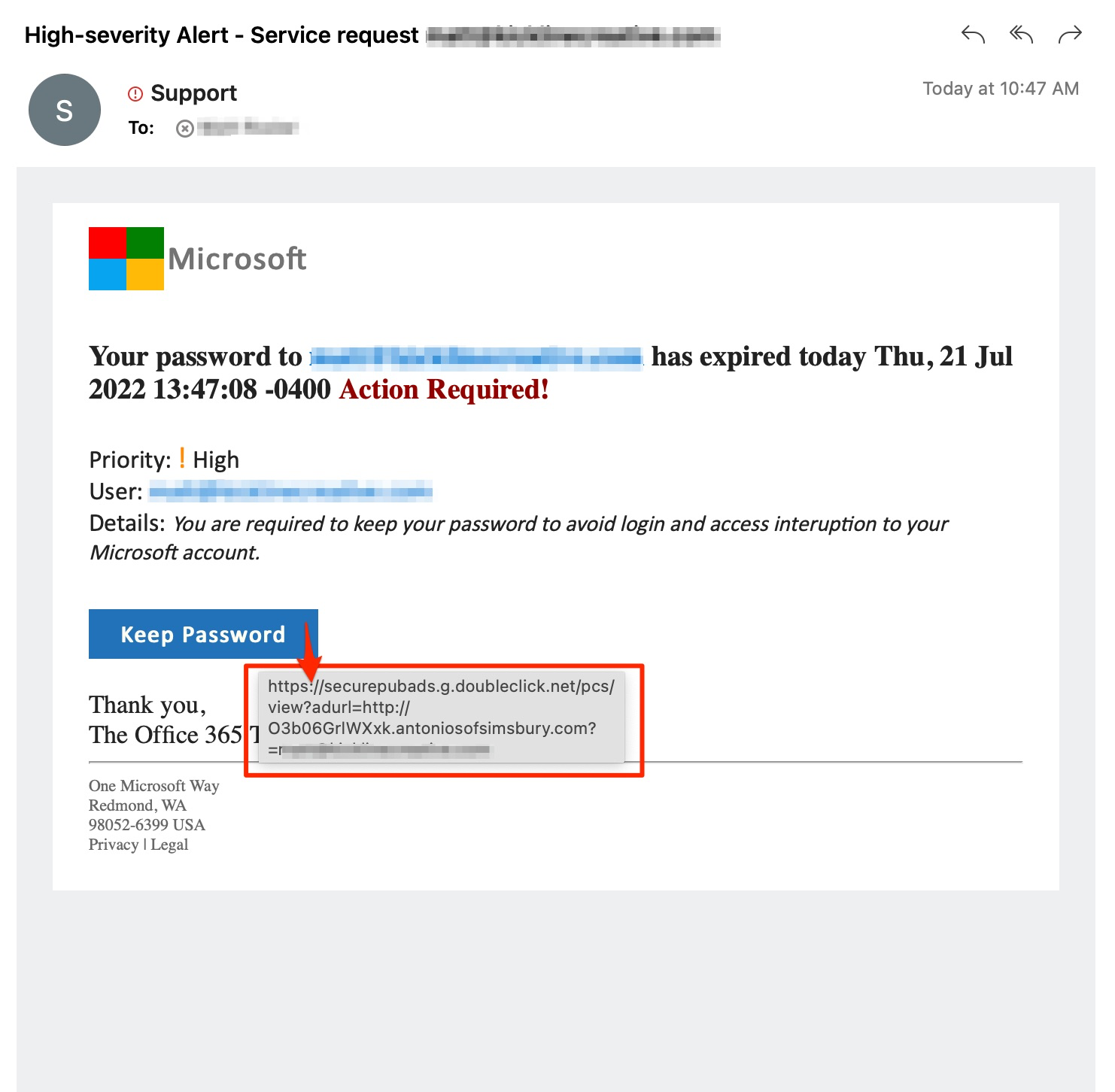
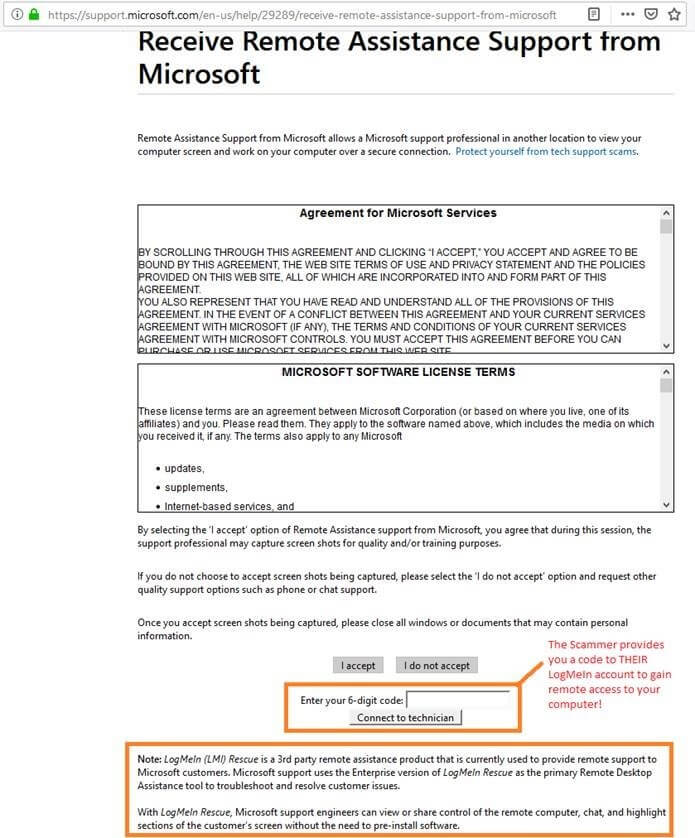
Tech support scams
In this scam, the attacker impersonates a technical support representative and contacts the employee to offer assistance with a computer issue, such as their account password has expired and they need to reset it. In these attacks, the threat actor may request remote access to the employee’s computer where they will have the ability to steal sensitive information or install malware.
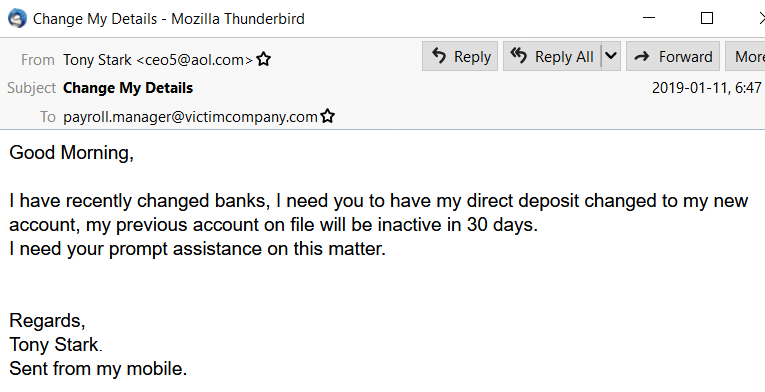
Payroll, wage and tax scams
This scam targets HR and payroll employees, typically during tax season. Threat actors will impersonate executives or HR personnel requesting a list of all employees including their wage and tax statement forms, which would allow the attacker to commit identity theft or file fraudulent tax returns. Alternatively, threat actors may also impersonate an employee at the company, requesting that their payroll gets redirected to another account due to a change in their bank. With the beginning of the year being tax season in the U.S., threat actors have been launching tax-related phishing scams against unsuspecting victims. There is definite cause for apprehension as in 2022, the Internal Revenue Service (IRS) identified $5.7 billion in tax fraud schemes.
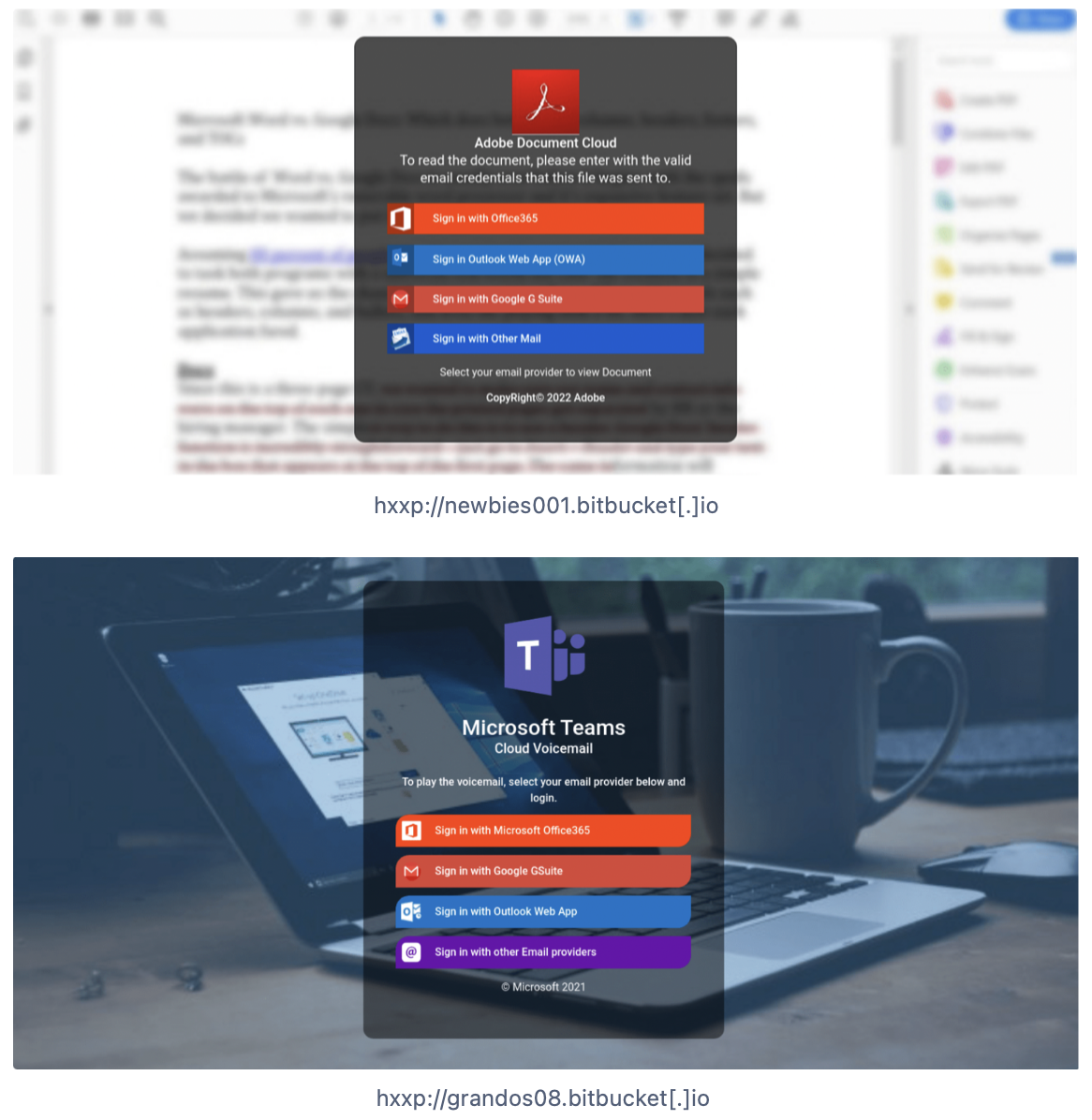
Fake Salary Increase
Emails impersonating a company’s HR department are being sent to employees with subject lines such as, “A Big Raise”, “Are you getting the raise you deserve?”, “Congratulations. Your salary is approved for increment,” and “You’re getting a pay raise.” The emails attempt to lure the employee into clicking on a link to a document that requires your Microsoft password in order to read it, such as in the examples below. Note, this is unfortunately a scam.
Brand protection with Bfore.Ai
Employee targeted scams are a serious threat to businesses, and unfortunately, they’ve only become more convincing and sophisticated by the increased use of brand impersonation and Artificial Intelligence. By providing regular training to employees, implementing strong security measures, and having a clear protocol in place for responding to these threats, businesses can help protect themselves against these types of cyber threats.
In the fight against these attacks to your business, innovative solutions are needed that can help you stay one step ahead of cyber criminals. This is where Bfore.Ai and our PreCrime Brand technology comes in to play. It works by identifying patterns and anomalies in data that may indicate the presence of a cyber threat specifically targeted towards your brand. This will allow you to take preemptive measures to protect your company against targeted threats, rather than simply reacting to them after the damage has already been done. This can help you save money, protect your brand reputation, and maintain the trust of your customers and stakeholders.
.png) Schedule a demo today to learn more about how Bfore.ai can help your company preempt brand attacks to defend your reputation!
Schedule a demo today to learn more about how Bfore.ai can help your company preempt brand attacks to defend your reputation!