
State Bank of India (SBI) a Fortune 500 company, is an Indian Multinational, Public Sector Banking and Financial services statutory body headquartered in Mumbai. The rich heritage and legacy of over 200 years, accredits SBI as the most trusted Bank by Indians through generations.
During our PreCrime internet scout of November 29th 2022 we identified suspicious markers across multiple vectors. One of those was this website spoof that could be targeting unsuspecting customers of SBI bank.
The Attack
Legitimate sites :
onlinesbi[.]sbi
bank[.]sbi
Malicious domains :
ritow-f3a33[.]web[.]app
ritow-f3a33[.]firebaseapp[.]com
poeee-a6464[.]firebaseapp[.]com
This attack shows a brand impersonation attack on the largest commercial bank in India, State Bank of India (SBI).
Malicious site
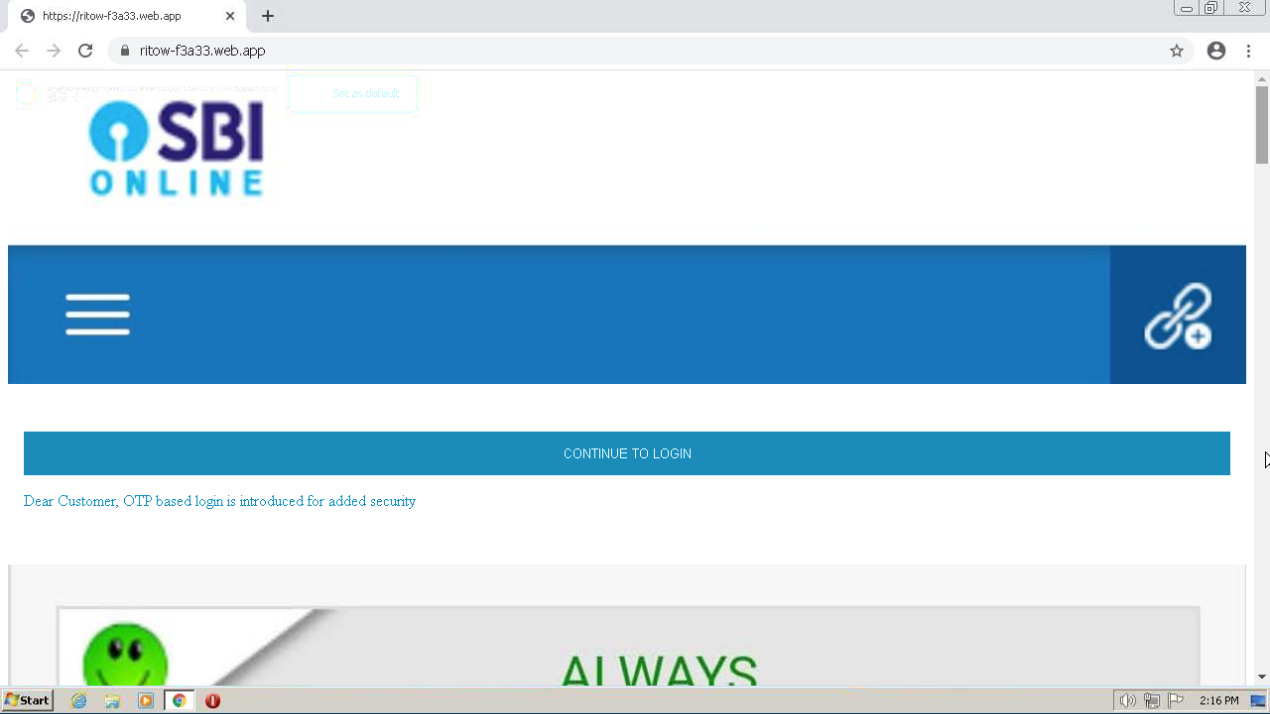
How does this attack work ?
- The domain leads users to a website where they can login to their SBI account using a One Time Password (OTP) to ensure added security. When clicking on ‘continue to login’, users are directed to a site where they are asked to reveal their username, password and mobile number.
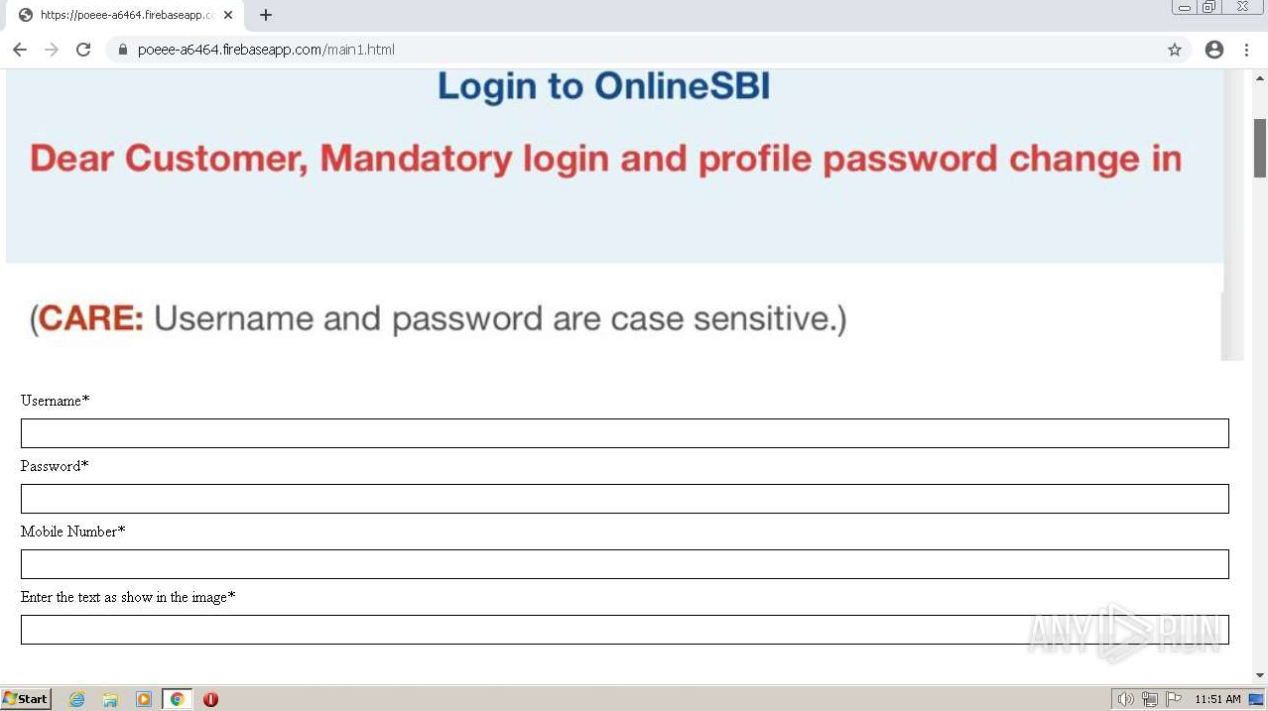
- The layout of the malicious site indicates that the threat actors will most likely target users via mobile phone through text messages of social media platforms. The threat actors will likely attempt to convince users that this is an urgent matter, a tactic often used to make victims feel a sense of urgency and thereby more likely to comply.
How do they trick users into believing the attack is real ?
-
Using branding from SBI including the same logo, colours and font.
-
The site includes information about how to keep yourself secure online and what to look out for to stay safe. As shown in the image below, the site only mentions recommendations that apply to their malicious site, such as, ensure that the URL has an SSL certificate, meaning that it begins with “https“ and includes a padlock symbol. This tactic is used by the threat actor in order to fool the victim into believing that they are on a secure website which they can verify themselves by checking the padlock. While sites with a padlock have generally been considered safe, threat actors are increasingly using valid SSL certificates to give the website an appearance of legitimacy.
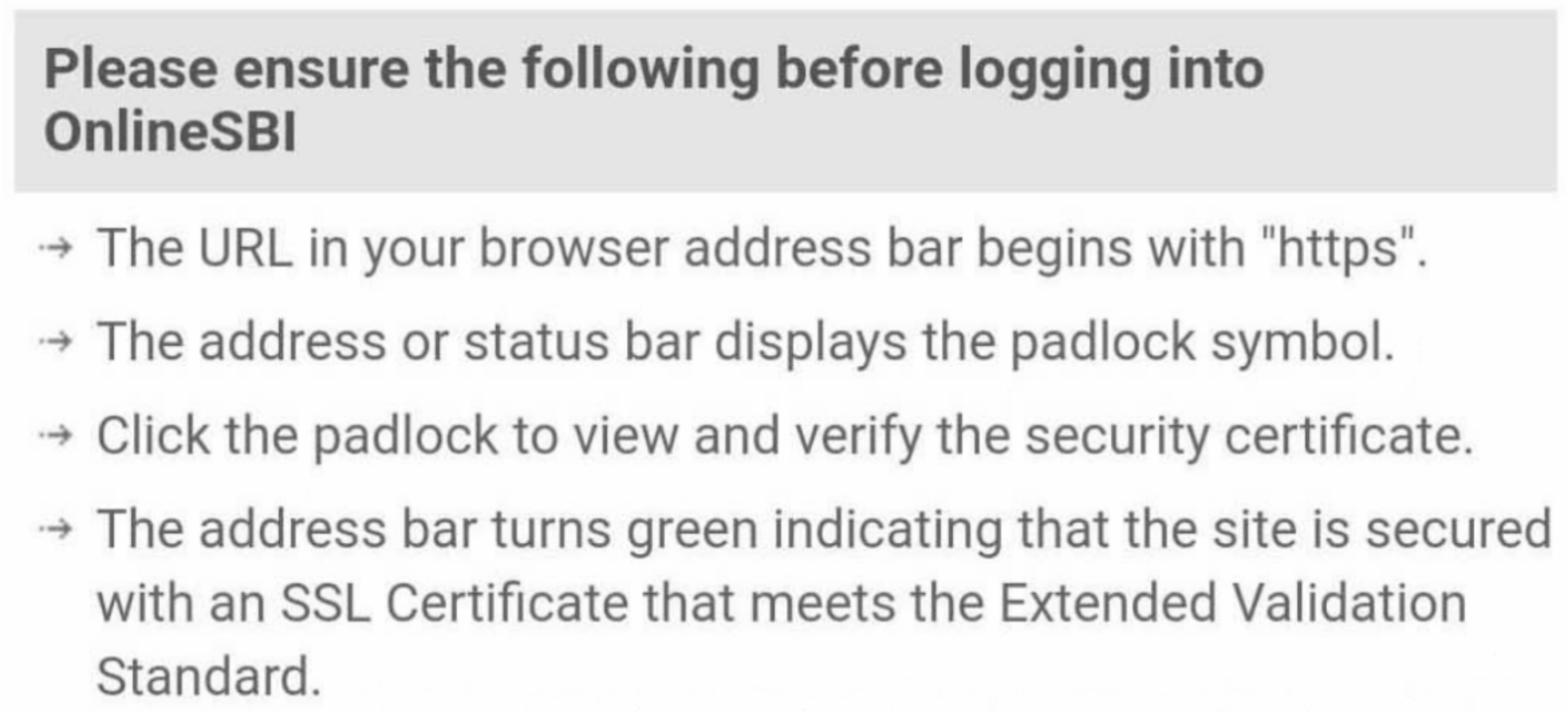
Why is this a threat ?
If successful, this attack would provide threat actors with access to sensitive personal information about the individual or corporate user, allowing threat actors to take control of their bank account and steal their money. Corporations using SBI would also be at risk of their internal network being compromised if their credentials used at SBI correspond to those they use for work.
Domain brand impersonation does not just lead to theft of sensitive personal information, but could also result in malware infection for both private consumers and global corporations depending on the target and end goal of the threat actor. This occurs when stolen credentials are sold on the dark web, giving other threat actors the ability to conduct further attacks against the user(s) such as ransomware attacks. Such attacks could pose serious consequences for the company, including high monetary costs, disrupting business operations, exposure of confidential data and reputational damage.
-
According to a report by the Reverse Bank of India, over the last seven years India has lost at least Rs 100 crore every day to bank fraud or scams, which equals to around 12 million USD lost every day to fraud.
-
With a yearly revenue of around 53 billion USD (4.07 trillion INR), a cyber incident of SBI could ultimately result in the loss of up towards 212 million USD (17 billion INR).
-
Companies connected to SBI could run the risk of a data breach which as of 2022 could result in the loss of around 4,35 million USD.
-
If individual consumers were to become a victim of this attempt to gain their personal information over the internet, they could lose between 2-3 thousand USD.
Identification and threat analysis
Technical Report
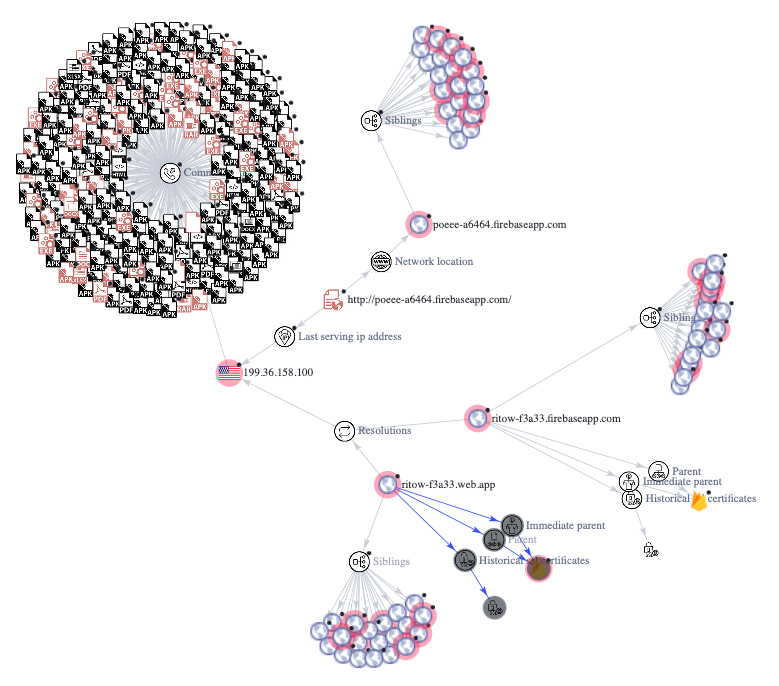
The technical report below helps emphasize the differences in terms of DNS records between the malicious domain, and the legitimate domain.
| Domain | ritow-f3a33[.]web[.]app
ritow-f3a33[.]firebaseapp[.]com poeee-a6464[.]firebaseapp[.]com |
onlinesbi[.]sbi
bank[.]sbi |
|---|---|---|
| Registrar | MarkMonitor, Inc. | 101domain GRS Limited |
| Registrant Organisation | Google LLC | State Bank Of India |
| Registrant Country | United States | India |
| Domain Age | 1 day old
Created 28 October 2022 |
2,223 days old
Created 28 October 2016 |
| Certificate | Issued by: Google Trust Services LLC
Issued to: firebaseapp[.]com/web[.]app Domain validated 25-10-2022 -> 23-01-2023 Valid for 3 months |
Issued by: DigiCert Inc
Issued to: State Bank Of India Organisation validated 01-06-2022 -> 01-06-2023 Valid for 1 year |
| Name Servers | N/A | NS1.101DOMAIN.COM
NS2.101DOMAIN.COM NS5.101DOMAIN.COM |
| Last seen active | 29 November 2022 | 29 November 2022 |
| IP address | 199.36.158.100
Mountain View, California, U.S. AS54113 Fastly, Inc. ISP: Fastly, Inc. |
103.209.96.177, 103.68.221.190
Navi Mumbai, Maharashtra, India AS45644 IT-Networking Department ISP: SBI-EMS |

How Bfore.Ai is protecting our customers
At Bfore.Ai, we work daily to ensure these phishing attacks get stopped before even reaching their targets. We are here to make your internet journey safer than it has ever been.
With more than 30K new malicious indicators per day we got you covered no matter where the attack comes from. Only 0.05% false positive rate, stop wasting time in false alerts chasing. By launching our PreCrime and PreEmpt technologies, we measure our anticipation from an attack starting, faster than attackers.
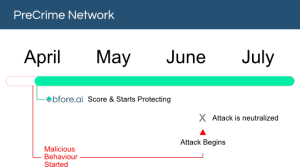
Accepting that the only defense is good detection, is accepting to be forever a victim. We believe in prevention more than response. Visit our website for more information !
Bfore.Ai’s recommendations
Every day, adversarial tactics become more collaborative, technologically advanced, and rapid – and at this rate, you simply can’t afford to wait for the next attack before you react. Here are some recommendations from our team :
-
If in doubt whether an email is legitimate, never click on any links. Go to the legitimate website’s domain instead via a search engine.
-
Always double check the domain name to make sure it is the legitimate one.
-
Never use the same credentials for work and personal accounts.
-
A padlock next to the domain name which generally proves that a website is secure, does not always mean that the website you are visiting is legitimate. Cyber criminals have started buying certificates to showcase the padlock on their malicious sites in order to fool site visitors.
-
Use different passwords for online banking and shopping sites, for example, so if one of your accounts becomes compromised your other accounts will remain safe.
-
Incorporate Multi Factor Authentication where possible to keep your accounts safe even if the credentials are compromised.
Appendix
This document and its contents do not constitute, and are not a substitute for, legal advice. The outcome of a Security Risk Assessment should be utilized to ensure that diligent measures are taken to lower the risk of potential weaknesses be exploited to compromise data.
Although the Services and this report may provide data that Client can use in its compliance efforts, Client (not Bfore.Ai) is ultimately responsible for assessing and meeting Client’s own compliance responsibilities. This report does not constitute a guarantee or assurance of Client’s compliance with any law, regulation or standard.






