.png)
Apple ID phishing scams represent genuine danger nowadays. Today there are 1.5 billion active Apple devices, which require Apple IDs to gain access to Apple services like Apple Music, App Store, iCloud, FaceTime, iMessage, and others.
During our PreCrime internet scout of November 2nd 2022 we identified suspicious markers across multiple vectors. One of those was this website spoof that could be targeting unsuspecting Chinese Apple customers.
The Attack
Target:
- Chinese Apple customers.
Possible threats:
-
Phishing campaign – luring customers to the site by sending them a message impersonating Apple stating that they need to login to their account to resolve some issue, with a link to the malicious domain where users can login.
-
Financial gain and identity theft – After luring users to the site, they are asked to login using their Apple ID, allowing threat actors to take over the customers account and steal their personal information.
With around 1 billion people using Apple products, the company is a popular target for threat actors due to their trusted name as well as large and global customer base, which is reflected in the thousands of Apple credentials currently for sale on dark web marketplaces.
The below domains attempt to trick customers into revealing their Apple ID credentials, which would allow the attacker to gain access to personal information stored on your Apple ID. Additionally, as seen in previous Apple scams, once a customer has logged into their Apple ID, they will most likely be asked to verify their account with details such as, name, address, social security number, credit card number, and so on.
According to SEON, if consumers were to fall for this scam they could lose between 3-9 thousand USD! With 51% of people using the same passwords for both their work and personal accounts, any leaked password would put other personal and work accounts that use the same email and password at risk of being hacked.
 Malicious site Malicious site |
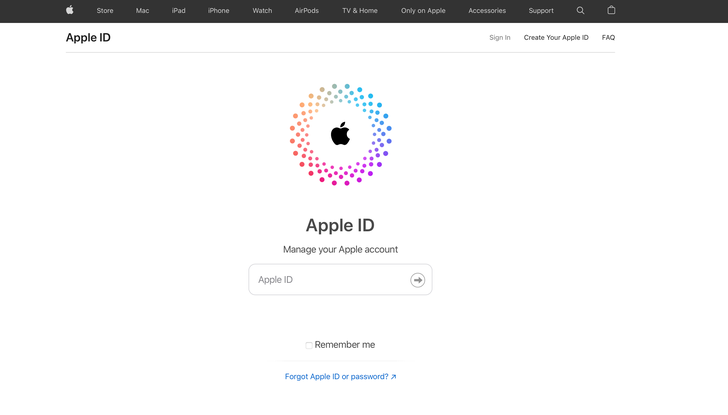
Legitimate site hxxps://appleid.apple[.]com/sign-in |
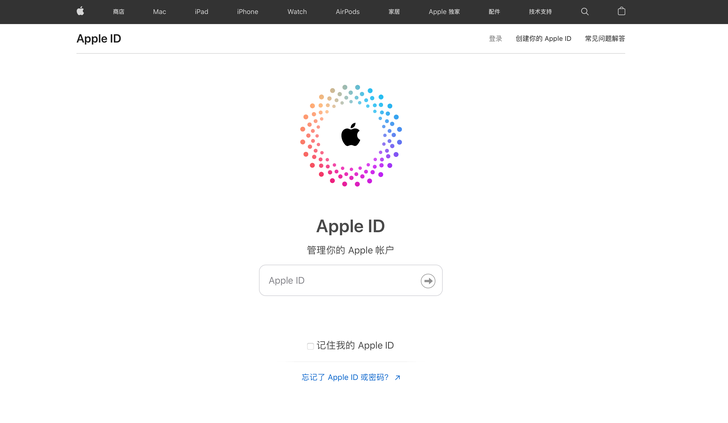 Legitimate login in China Legitimate login in China |
Technical Breakdown
Threat Indicators
-
Malicious domain impersonating Apple, asking customers to login using their Apple ID.
-
DNS records of malicious domain completely different to Apple
-
Newly registered sites – October 22-30 2022
-
No registered SSL certificates
Detection and Threat Analysis
The malicious domains created October 22-30, 2022, have been targeting Apple Inc. (apple[.]com), one of the world’s largest multinational technology company.
-
The malicious domains all show an Apple ID login page. The sites are all attempting to replicate the Chinese apple login page. All the links on the malicious sites listed at the top of the page that would normally lead you to the apple store (‘Store’), or to their product pages (‘Mac’, ‘iPad’, ‘iPhone’, ‘Watch’…), all lead the user back to the same login page.
-
The DNS records are completely different to the DNS records of the legitimate website (apple.com). The main point of interest is that the legitimate domain has their own ASN (AS714 Apple Inc.) which they use for all their registered domain. The malicious domains are under a Gnet Inc. ASN (AS9294). See further details below.
-
With no registered SSL certificates the domains have no site security, indicating malicious intent. Every legitimate domain will always ensure SSL certificates in order to verify themselves as a company and protect their customers.
-
As shown in the graph below, the threat actor is using a different IP address for each malicious domain. However, they all use the same ASN provider, gnet agency (AS9294 Gnet Inc).
Graph
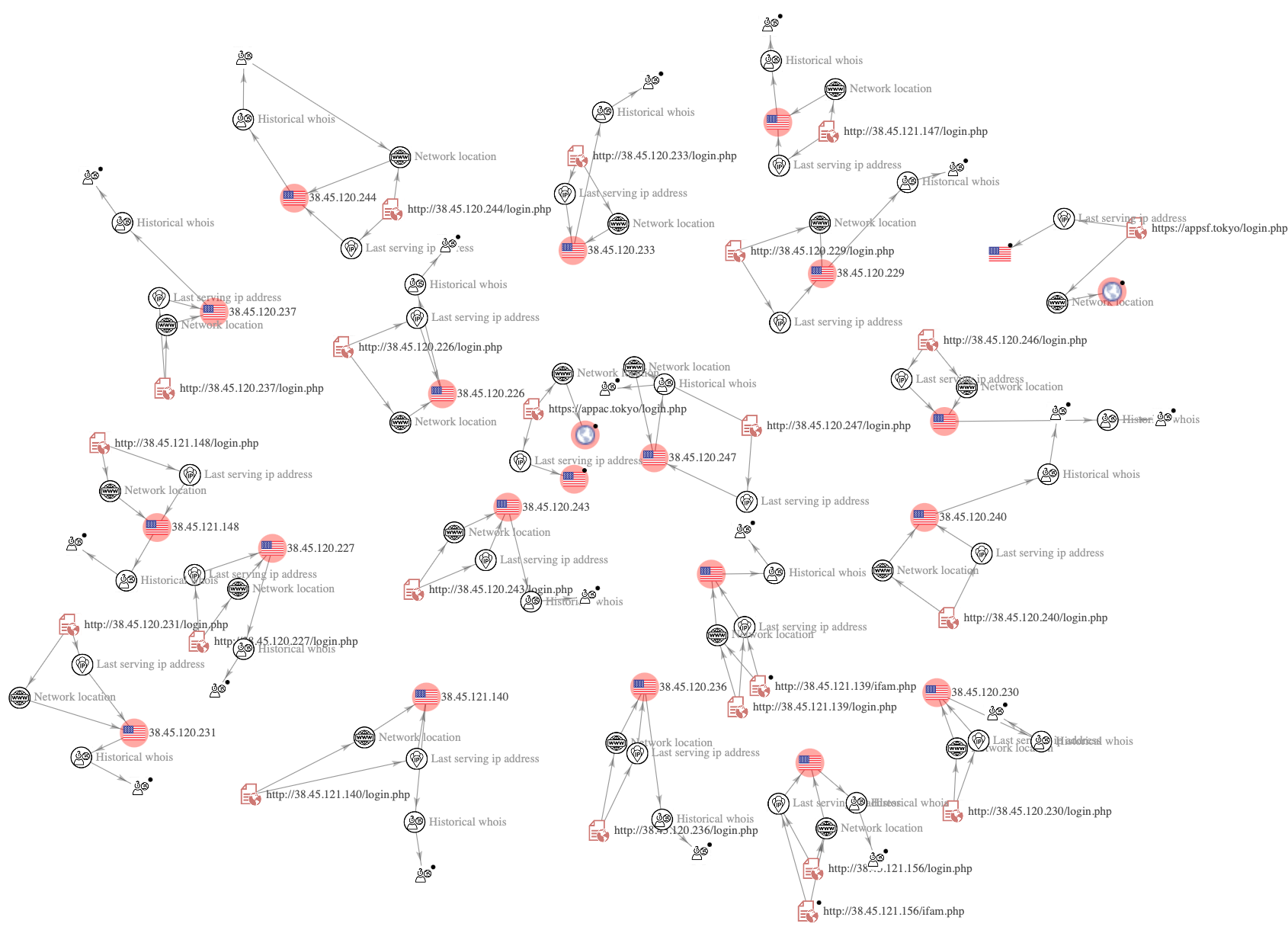 VirusTotal Graph
VirusTotal Graph
WhoIs Record
| Creation date | IP address | |
|---|---|---|
| hxxp.apple.com | 19 February 1987 | 17.253.144.10
California, United States AS714 Apple Inc. |
| hxxp://38.45.121.139/login[.]php
hxxp://38.45.121.139/ifam[.]php |
21 October 2022 | 38.45.121.139
Sai Kung, Hong Kong AS9294 Gnet Inc. |
| hxxp://38.45.121.140/login[.]php | 22 October 2022 | 38.45.121.140
Sai Kung, Hong Kong AS9294 Gnet Inc. |
| hxxp://38.45.121.147/login[.]php | 24 October 2022 | 38.45.121.147
Sai Kung, Hong Kong AS9294 Gnet Inc. |
| hxxp://38.45.121.148/login[.]php | 24 October 2022 | 38.45.121.148
Sai Kung, Hong Kong AS9294 Gnet Inc. |
| hxxp://38.45.121.156/login[.]php
hxxp://38.45.121.156/ifam[.]php |
26 October 2022 | 38.45.121.156
Sai Kung, Hong Kong AS9294 Gnet Inc. |
| hxxp://38.45.120.226/login[.]php | 26 October 2022 | 38.45.120.226
Sai Kung, Hong Kong AS9294 Gnet Inc. |
| hxxp://38.45.120.227/login[.]php | 26 October 2022 | 38.45.120.227
Sai Kung, Hong Kong AS9294 Gnet Inc. |
| hxxp://38.45.120.229/login[.]php | 27 October 2022 | 38.45.120.229
Sai Kung, Hong Kong AS9294 Gnet Inc. |
| hxxp://38.45.120.230/login[.]php | 27 October 2022 | 38.45.120.230
Sai Kung, Hong Kong AS9294 Gnet Inc. |
| hxxp://38.45.120.231/login[.]php | 27 October 2022 | 38.45.120.231
Sai Kung, Hong Kong AS9294 Gnet Inc. |
| hxxp://38.45.120.233/login[.]php | 27 October 2022 | 38.45.120.233
Sai Kung, Hong Kong AS9294 Gnet Inc. |
| hxxp://38.45.120.236/login[.]php | 28 October 2022 | 38.45.120.236
Sai Kung, Hong Kong AS9294 Gnet Inc. |
| hxxp://38.45.120.237/login[.]php | 28 October 2022 | 38.45.120.237
Sai Kung, Hong Kong AS9294 Gnet Inc. |
| hxxp://38.45.120.240/login[.]php | 28 October 2022 | 38.45.120.240
Sai Kung, Hong Kong AS9294 Gnet Inc. |
| hxxp://38.45.120.243/login[.]php | 29 October 2022 | 38.45.120.243
Sai Kung, Hong Kong AS9294 Gnet Inc. |
| hxxp://38.45.120.244/login[.]php | 29 October 2022 | 38.45.120.244
Sai Kung, Hong Kong AS9294 Gnet Inc. |
| hxxp://38.45.120.246/login[.]php | 30 October 2022 | 38.45.120.246
Sai Kung, Hong Kong AS9294 Gnet Inc. |
| hxxp://38.45.120.247/login[.]php | 30 October 2022 | 38.45.120.247
Sai Kung, Hong Kong AS9294 Gnet Inc. |
How Bfore.Ai is protecting our customers
At Bfore.Ai, we work daily to ensure these phishing attacks get stopped before even reaching their targets. We are here to make your internet journey safer than it has ever been.
With more than 30K new malicious indicators per day we got you covered no matter where the attack comes from. Only 0.05% false positive rate, stop wasting time in false alerts chasing. By launching our PreCrime and PreEmpt technologies, we measure our anticipation from an attack starting, faster than attackers.
Accepting that the only defense is good detection, is accepting to be forever a victim. We believe in prevention more than response. Visit our website for more information !
Bfore.Ai’s recommendations
Every day, adversarial tactics become more collaborative, technologically advanced, and rapid – and at this rate, you simply can’t afford to wait for the next attack before you react. Here are some recommendations from our team :
- Pay close attention to the URL
- Check connection security indicators (the lock)
- Read emails carefully
- Look for trust seals
Appendix
This document and its contents do not constitute, and are not a substitute for, legal advice. The outcome of a Security Risk Assessment should be utilized to ensure that diligent measures are taken to lower the risk of potential weaknesses be exploited to compromise data.
Although the Services and this report may provide data that Client can use in its compliance efforts, Client (not Bfore.Ai) is ultimately responsible for assessing and meeting Client’s own compliance responsibilities. This report does not constitute a guarantee or assurance of Client’s compliance with any law, regulation or standard.





