
DHL is a German logistics company providing courier, package delivery and express mail service, which is a division of the German logistics firm Deutsche Post. The company group delivers over 1.6 billion parcels per year.
During our PreCrime internet scout of October 12th 2022 we identified suspicious markers across multiple vectors. One of those was this website spoof that could be targeting unsuspecting users.
The Attack
Target:
- DHL customers
Possible threats:
- Phishing campaign – luring customers to the site by sending them a message impersonating DHL stating that there was a failed delivery attempt, with a link to the malicious domain where users can solve the issue.
- Financial gain and identity theft – After luring users to the site, they are asked to confirm their address and pay shipping costs to receive their package, allowing threat actors to steal the customers PII and money.
This domain is one among many targeting DHL at the moment. According to CheckPoint, DHL was the most imitated brand in Q3, where the they accounted for 22% of all phishing attempts globally.
This aligns with a statement issued by DHL in June 2022, where they announced that they are “currently the target of a major global scam and phishing attack”.
In general companies such as FedEx, Netflix and DHL are popular targets for brand impersonation due to their trusted name as well as large and global customer base. DHL will most likely see a continued increase in scams targeting their brand in the coming months as they did last year in Q4 with holidays such as Black Friday, Cyber Monday and Christmas coming up. During these holidays we generally see an increase in online purchases and package deliveries, giving threat actors a higher chance of succeeding in impersonating companies like DHL. Therefore, customers should stay vigilant and always use the legitimate domain dhl.com when checking their parcels.

When clicking on continue :




Technical Breakdown
Threat Indicators
- Malicious domain impersonating DHL and asking customers to pay delivery costs due to incorrect address.
- DNS records of malicious domain completely different to DHL
- Newly registered site – October 10 2022
- SSL certificate expires after three months
Detection and Threat Analysis
The malicious domain, international-package.pubchaplin[.]it created October 10, 2022, has been targeting DHL (dhl[.]com), a market leading German logistics company that delivers billions of parcels worldwide every year.
- The malicious domain leads users to a duplicate DHL website where customers are told that their package could not be delivered due to an incorrect delivery address. Therefore, instructing customers to click on continue where they are asked to enter in their address details and later credit card details to pay for the shipping cost. Doing so will lead to the threat actor gaining access to the customers private details, including name, home address, phone number and bank details. This would give the threat actor the ability to steal the customers identity and their money.
- The DNS records are completely different to the DNS records of the legitimate website. The main point of interest is that the legitimate domain is registered under the company name (Deutsche Post AG), whereas the malicious one does not provide details of this. Legitimate domains will always publicly show the registrar organisation for validity. See further details below.
- The registered SSL certificate expires after three months and is issued by a non-trusted certificate issuer (Let’s Encrypt), indicating malicious intent.

DNS Records

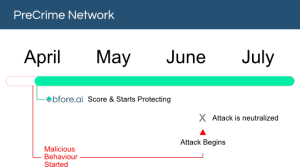
How Bfore.Ai is protecting our customers
At Bfore.Ai, we work daily to ensure these phishing attacks get stopped before even reaching their targets. We are here to make your internet journey safer than it has ever been.
With more than 30K new malicious indicators per day we got you covered no matter where the attack comes from. Only 0.05% false positive rate, stop wasting time in false alerts chasing. By launching our PreCrime and PreEmpt technologies, we measure our anticipation from an attack starting, faster than attackers.
Accepting that the only defense is good detection, is accepting to be forever a victim. We believe in prevention more than response. Visit our website for more information !
Bfore.Ai‘s recommendations
Every day, adversarial tactics become more collaborative, technologically advanced, and rapid – and at this rate, you simply can’t afford to wait for the next attack before you react. Here are some recommendations from our team :
- Pay close attention to the URL
- Check connection security indicators (the lock)
- Read emails carefully
- Look for trust seals
Appendix
This document and its contents do not constitute, and are not a substitute for, legal advice. The outcome of a Security Risk Assessment should be utilized to ensure that diligent measures are taken to lower the risk of potential weaknesses be exploited to compromise data.
Although the Services and this report may provide data that Client can use in its compliance efforts, Client (not Bfore.Ai) is ultimately responsible for assessing and meeting Client’s own compliance responsibilities. This report does not constitute a guarantee or assurance of Client’s compliance with any law, regulation or standard.





